Securing your environment becomes a critical priority as your organization embarks on its journey to the cloud. IBM Cloud offers unparalleled scalability, flexibility, and access to advanced technologies, but you may have concerns about unique security challenges during onboarding. Developing a comprehensive cloud security strategy on IBM Cloud is essential for safeguarding your critical assets, managing identities, detecting threats, and preparing for incidents.
Table of Contents
- Getting Started with IBM Cloud Onboarding
- Understanding Your Cloud Footprint on IBM Cloud
- Building a Threat Detection Program on IBM Cloud
- Investigating and Responding to Incidents on IBM Cloud
- Embracing Secure by Design Principles on IBM Cloud
- Modernizing Identity Management on IBM Cloud
- Tackling Misconfigurations and Cloud Identity Challenges
- Leveraging IBM Cloud Encryption and Key Management
- Addressing Complex Cloud Security Challenges on IBM Cloud
- Future-Proofing Cloud Security on IBM Cloud
- Additional Resources and Support
- Conclusion
- Frequently Asked Questions (FAQ)
- References and Resources
- Call to Action
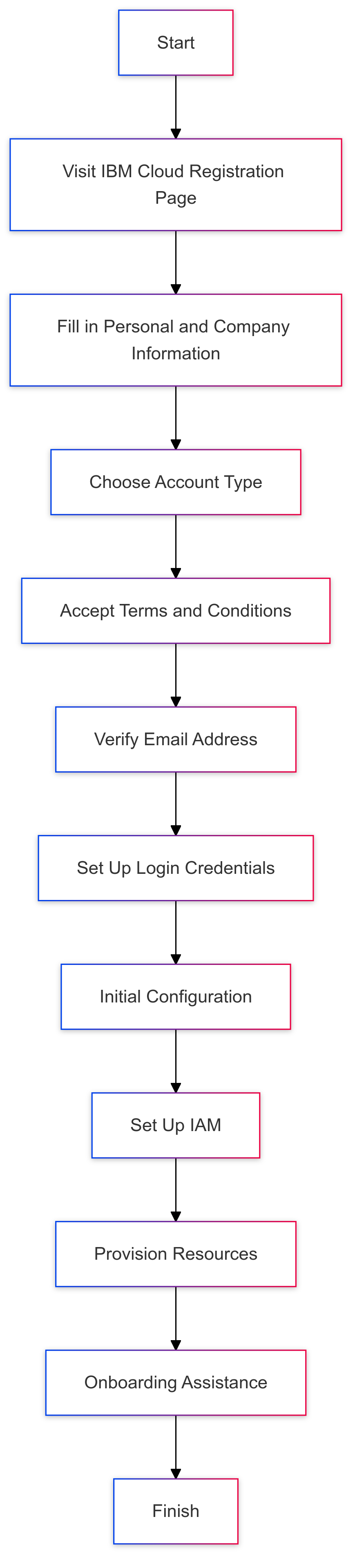
1. Getting Started with IBM Cloud Onboarding
Successfully onboarding onto IBM Cloud involves careful planning and execution. This section guides you through
the initial steps to set up your IBM Cloud environment.
Ready to embark on your IBM Cloud journey?
Contact Our IBM Cloud Onboarding Specialists |
Explore IBM Cloud Services |
Join the IBM Cloud Community