
Introduction
Imagine the chaos unleashed in 2017 when the WannaCry ransomware spread like wildfire, crippling hospitals and businesses by encrypting vital data. This attack underscored the catastrophic consequences of weak cryptographic implementations when cryptography fails to shield our digital lives. The same cryptographic principles at risk in incidents like WannaCry underpin technologies like blockchain, demonstrating the far-reaching importance of cryptography. Today, cryptography is indispensable in anchoring IT security, propelled by the urgent need to shield the growing volumes of sensitive digital data. The dependence on online platforms for personal, financial, and governmental exchanges highlights the need for impenetrable communication channels. Cryptography secures data against unauthorized access through encryption, making it indecipherable to outsiders and forming a solid barrier against diverse cyber threats.
Securing personal and financial details, intellectual property, and national security data through confidentiality is a top priority. Encryption transforms readable data into a secure format, decipherable only by authorized key holders. This encryption is crucial for both stored data and data in transit, demanding a strategic choice between symmetric and asymmetric encryption tailored to organizational needs. Managing encryption keys effectively, including their creation, storage, and deletion, is vital for preserving data confidentiality, especially as organizations expand.
Integrity confirms that data remains unchanged in storage or transmission, protecting against unauthorized alterations. Cryptographic hashing creates a distinct data signature, allowing for alteration detection. Digital signatures use asymmetric encryption to verify message sources and integrity, ensuring sensitive communications like contracts and software updates are authentic.
Cryptography indirectly supports availability, defending against DDoS attacks and ransomware. It secures data backups, enabling recovery from ransomware without yielding to demands.
The evolution of wireless security standards from WPA to WPA3 demonstrates the ongoing refinement of cryptographic practices to tackle new security threats. WPA3 introduces superior encryption and protection, urging organizations to adapt their IT infrastructure for enhanced security.
As quantum computing emerges, the threat of rendering some existing cryptographic algorithms obsolete becomes increasingly palpable. Entities such as NIST spearhead research initiatives dedicated to formulating quantum-resistant algorithms, which necessitate expanded key sizes for symmetric methods. Concurrently, hash functions face increasingly formidable obstacles. In response, organizations must adopt a stance of cryptographic agility, enabling the seamless incorporation of newer, more secure algorithms to counteract the rapidly advancing threat landscape.
Blockchain technology relies on cryptographic hash functions and digital signatures for secure, decentralized operations. Beyond cryptocurrencies, blockchain promises to revolutionize supply chain management, digital identity verification, and secure voting; however, this widespread impact remains contingent on the continued advancement of cryptographic methods, some still in early stages, such as secure multi-party computation and fully practical homomorphic encryption.
Navigating the complexities of digital data communication and storage in an interconnected world underscores the critical role of cryptography in IT security. Future research and innovation are imperative for addressing sophisticated cyber threats and ensuring the protection of digital assets in an evolving technological landscape.
Cryptography in IT Security
Encryption Methods and Their Implementation – Cryptography is the cornerstone of data security to ensure confidentiality, integrity, and availability across digital communications. The progression from symmetric encryption to more sophisticated methods like asymmetric encryption and hybrid systems illustrates the dynamic nature of cryptography in overcoming challenges related to key distribution, scalability, and the balance between security and efficiency.
Symmetric Encryption
The Speed and Security Basis – Symmetric encryption, employing a single key for encryption and decryption, offers an efficient method for securing vast data. However, this simplicity brings challenges in key distribution and management. The risk of key interception necessitates innovative solutions like the Diffie-Hellman key exchange for secure key sharing over unsecured channels. Despite its effectiveness for bulk data encryption, symmetric encryption’s scalability issues call for advanced key management strategies to address key exchange, storage, and rotation challenges.
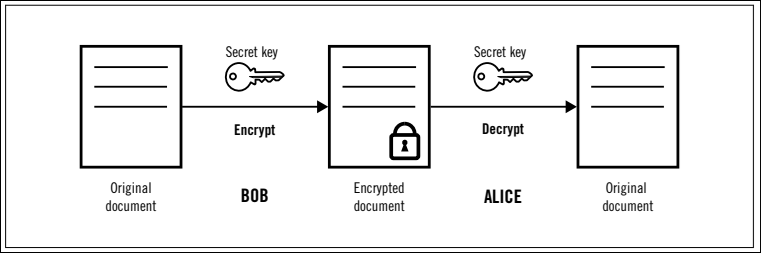
Figure 1. Symmetric Encryption
Symmetric key exchange involves two parties, Alice, and Bob, exchanging a shared secret key to encrypt and decrypt messages. Here’s a simple diagram illustrating this process:
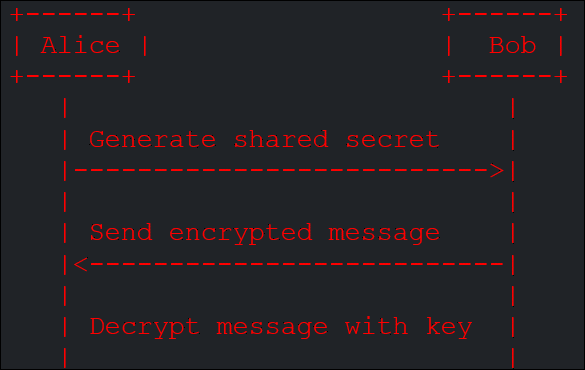
Figure 2. In this diagram, Alice and Bob generate a shared secret key and use it to encrypt and decrypt messages.
Asymmetric Encryption
Addressing the Key Distribution Challenge – Asymmetric encryption provides a robust solution to symmetric encryption’s key distribution issues. Using related key pairs enables secure communication over unsecured channels without shared secrets. This method enhances confidentiality and authentication and underpins digital signatures for verifying message integrity and origin. In hybrid models, asymmetric encryption for key exchange combines the efficiency of symmetric encryption with secure key distribution.
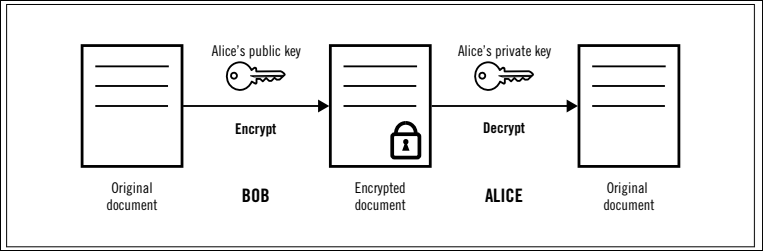
Figure 3. Asymmetric Encryption
Asymmetric key exchange involves two parties, Alice, and Bob, exchanging public keys to encrypt and decrypt messages. Here’s a simple diagram illustrating this process:
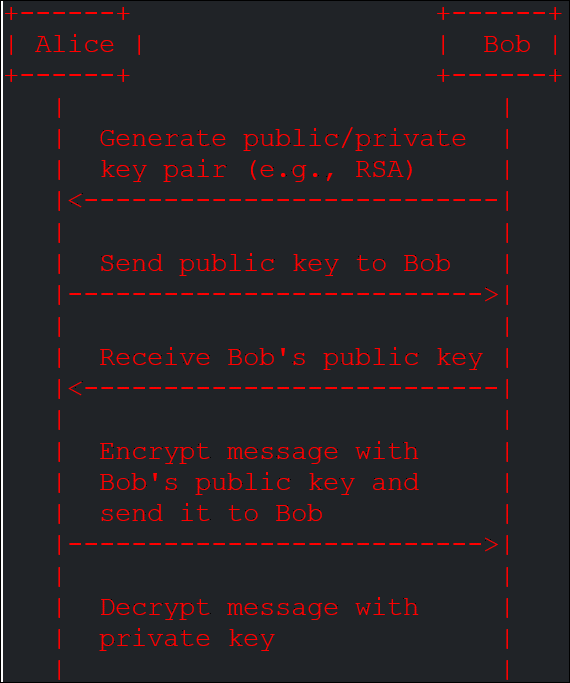
Figure 4. In this diagram, Alice and Bob generate public/private key pairs and use them to encrypt and decrypt messages.
Hybrid Encryption
Marrying Security and Efficiency – Hybrid encryption represents a strategic combination of symmetric and asymmetric encryption, optimizing security and performance. It employs the speed of symmetric encryption for data encryption and asymmetric encryption for initial key sharing. This blend ensures message confidentiality and streamlines key management, making it suitable for various applications, from secure messaging to complex key management.
Digital Signatures and Elliptic Curve Cryptography (ECC)
Key Management and Security Protocols – Digital signatures leverage asymmetric encryption to confirm message integrity and origin, which is crucial for secure digital contracts and software distribution. Furthermore, Elliptic Curve Cryptography offers a resource-efficient alternative to traditional RSA, particularly beneficial for devices with limited processing power, with its smaller key sizes enabling quicker operations and reduced storage demands.
Certificate Authorities and the Trust Model – Certificate Authorities play a central role in the digital trust model, authenticating public keys with digital certificates. Effective certificate management, covering certificate issuance, renewal, and revocation, is essential for encrypted communication security. As organizations deal with cryptographic implementation complexities, challenges in key management, scalability, and defense against side-channel attacks call for ongoing innovation and adherence to best practices.
In conclusion, cryptography in IT security is characterized by continuous evolution, addressing the diverse challenges of digital communication. From basic symmetric encryption to advanced hybrid models, the development of cryptographic methods demonstrates an unwavering commitment to securing the digital domain against emerging threats.
Failure Story – The Heartbleed Catastrophe
In 2014, the “Heartbleed” vulnerability sent shockwaves through the cybersecurity world. A seemingly insignificant coding error in the widely used OpenSSL library, responsible for securing web traffic, left a gaping hole through which attackers could extract sensitive data from supposedly secure servers, including passwords and encryption keys. The fallout exposed the fragile reality of real-world cryptographic implementation. Poor code review, insufficient testing, and slow patching response exacerbated the situation, highlighting the far-reaching impact when seemingly straightforward processes in encryption deployment break down.
Heartbleed starkly demonstrates that it’s not only robust algorithms but also their flawless implementation that are the linchpin of cryptographic security. As such, ongoing investment in coding best practices, rigorous security auditing, and timely response to vulnerabilities remain as crucial as theoretical cryptographical advances.
The Dynamic Landscape of Cryptography: A Historical Timeline
| Year | Cryptography Developments | Security Threats |
| 1977 | RSA algorithm introduced | – |
| 1985 | First published suggestion of using elliptic curve cryptography | – |
| 1991 | Phil Zimmermann releases PGP | – |
| 1994 | SSL encryption protocol released by Netscape | – |
| 1997 | Ciphersaber, an encryption system based on RC4 | – |
| 2001 | Microsoft and its allies vow to end “full disclosure” of security vulnerabilities | – |
| 2004 | The hash MD5 is shown to be vulnerable to practical collision attack | – |
| 2011 | Cryptographic key management and cryptographic key establishment methods patented | – |
| 2012 | Flame malware discovered, using MD5 collisions to forge Windows code-signing certificate | Flame Malware |
| 2014 | Heartbleed bug in OpenSSL | Heartbleed |
| 2017 | WannaCry ransomware attack | WannaCry |
| 2021 | Quantum-resistant cryptographic algorithms selected for standardization | – |
Conclusion and Future Directions in Cryptography
As the digital and quantum eras intersect, opportunities and challenges fill cryptography’s future path. The field must prepare for quantum computing’s impact and embrace the burgeoning realms of privacy and security in a world growing ever more connected.
Quantum Resilience
Gearing Up for a Post-Quantum Reality – The advent of quantum computing presents a formidable challenge to existing cryptographic standards. Initiatives like NIST’s Post-Quantum Cryptography Standardization program highlight the need to develop quantum-resistant algorithms proactively. Although the time horizon for full-fledged quantum computers capable of breaking current encryption might still be years away, emphasizing crypto agility or the capability to transition seamlessly between cryptographic standards as new threats and vulnerabilities emerge is essential for future-proofing digital infrastructures. The time to start planning and gradually integrating post-quantum solutions is now.
Advancing Privacy with Sophisticated Cryptographic Methods – Privacy enhancing technologies, especially homomorphic encryption, and zero-knowledge proofs, promises to expand the horizons of data confidentiality and secure computation. Homomorphic encryption enables the processing of encrypted data, paving the way for secure cloud computing and AI model training collaborations. Zero-knowledge proofs offer a means to verify truth without exposing underlying data, which is crucial for secure voting and private digital transactions. For example, a zero-knowledge proof could allow you to prove your age without revealing your birthdate.
Zero-knowledge proof is a method by which one party (the prover) can prove to another party (the verifier) that they know a secret value, without revealing the value itself. Here’s a simple diagram illustrating how a zero-knowledge proof might work:
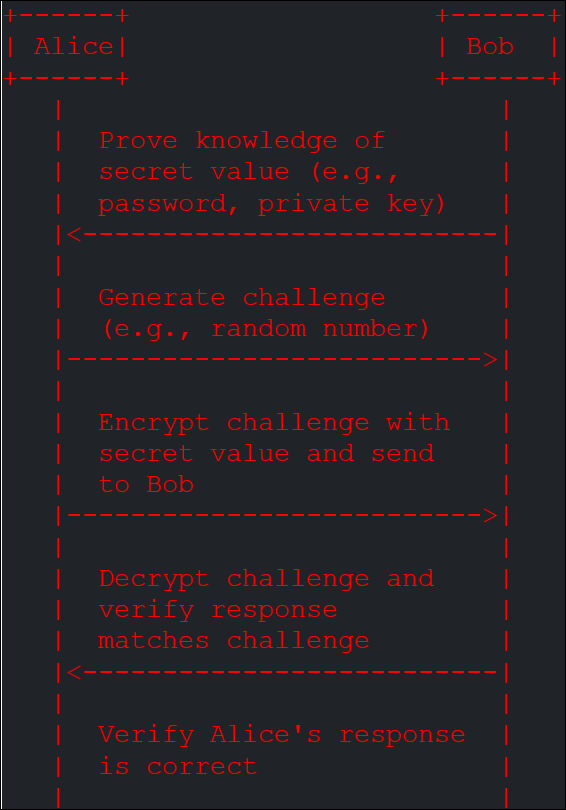
Figure 5. In this diagram, Alice proves to Bob that she knows a secret value without revealing the value itself. Bob generates a challenge (e.g., a random number), and Alice encrypts it with her secret value and sends it back to Bob. Bob then decrypts the response and verifies that it matches the challenge.
Cryptography’s Pivotal Role in IoT Security The Internet of Things introduces unique cryptographic challenges, necessitating approaches that consider device constraints, ensure device integrity, and manage identities and access effectively. Prioritizing lightweight cryptography, such as the NIST-standardized Ascon algorithm and secure boot mechanisms, is key to creating a secure IoT framework where privacy and authentication are paramount. Lightweight cryptography provides essential security for devices like medical sensors or smart home devices with limited computing power.
SMPC
Fostering Secure, Confidential Collaborations Secure Multi-Party Computation allows for private joint computations, opening doors to secure voting, data sharing, and analytical collaborations. This technology ensures the privacy of individual inputs throughout the computational process, ushering in a new era of confidentiality in collective data analysis. In e-voting, SMPC could enable transparent and verifiable elections while protecting individual voter choices. Similarly, healthcare providers could employ SMPC to collaborate on research without exposing sensitive patient information, furthering medical advancements while safeguarding privacy.
Addressing the Regulatory and Ethical Landscape
Implementing cryptographic solutions requires navigating a complex regulatory and ethical terrain, balancing user privacy against national security. As cryptographic technology advances, understanding its societal impact becomes increasingly crucial. Dialogue among technologists, policymakers, and the public is vital for ensuring that cryptographic innovations bolster individual freedoms and privacy.
A Unified Call to Action
Cryptography’s future rests not only in the hands of cryptographers but in a collaborative effort encompassing academia, industry, and governance. This collective journey involves exploring uncharted research avenues, anticipating, and neutralizing emerging threats, and ensuring that cryptographic practices evolve alongside technological and societal shifts. As we embark on this uncertain voyage, the cryptographic community must remain alert, innovative, and cooperative to protect the digital frontiers. A shared sense of responsibility among researchers, developers, and those governing IT infrastructure will prove critical in mitigating future risks like the devastating Heartbleed event. Through these efforts, cryptography will continue securing our digital existence.
Cryptography’s dynamic nature mandates readiness for future challenges and the seizing of opportunities offered by technological advancements to enhance security and privacy. The path forward is intricate, balancing innovation with ethical considerations, but cryptography will continue securing our digital existence through these efforts.
References
- McDonald1, Papadopoulos2, Pitropakis3 et al. (2022). Ransomware: Analysing the Impact on Windows Active Directory Domain Services. Sensors. Retrieved from https://ictjournal.icict.org.zm/index.php/zictjournal/article/view/19
- Fazri1, Kusuma2, Rahmawan3 et al. (2023). Implementing Artificial Intelligence to Reduce Marine Ecosystem Pollution. itsdi. Retrieved from https://aptikom-journal.id/index.php/itsdi/article/view/579
- Mavroeidis, V., Vishi, K., Zych, M. D., et al. (2018). The Impact of Quantum Computing on Present Cryptography. International Journal of Advanced Computer Science and Applications (IJACSA), 9(3). Retrieved from https://thesai.org/Publications/ViewPaper?Volume=9&Issue=3&Code=ijacsa&SerialNo=54
- Vashi, D. (2019). Performance of Symmetric and Asymmetric Encryption Techniques for Attribute Based Encryption. International Journal of Recent Technology and Engineering (IJRTE), 8(1S4). Retrieved from https://www.ijrte.org/portfolio-item/C6597098319/
- (2020). Comparing Symmetric and Asymmetric cryptography in message encryption and decryption by using AES and RSA algorithms. Journal of Xi’an University of Architecture & Technology (JXAT), XII(III). Retrieved from https://xajzkjdx.cn/gallery/271-mar2020.pdf
- Durumeric, Z., Li, F., Kasten, J., et al. (2014). The Matter of Heartbleed. Retrieved from https://dl.acm.org/doi/10.1145/2663716.2663755
- Gentry, C., Groth, J., Ishai, Y., et al. (2014). Using Fully Homomorphic Hybrid Encryption to Minimize Non-interative Zero-Knowledge Proofs. Journal of Cryptology. Retrieved from https://link.springer.com/article/10.1007/s00145-014-9184-y
- Chiadighikaobi, I. R., Katuk, N. (2021). A Scoping Study on Lightweight Cryptography Reviews in IoT. Baghdad Science Journal. Retrieved from https://bsj.uobaghdad.edu.iq/index.php/BSJ/article/view/6218
- Yan, S., Liu, C., Wang, M.-Q., et al. (2018). Promoting Data Circulation by Secure Multi-party Computation and Blockchain. DTCSE. Retrieved from https://www.dpi-journals.com/index.php/dtcse/article/view/24542
- Michael, K., & Michael, M. G. (2014). The regulatory considerations and ethical dilemmas of location-based services (LBS). Information Technology and People. Retrieved from https://www.emerald.com/insight/content/doi/10.1108/ITP-12-2012-0156/full/html