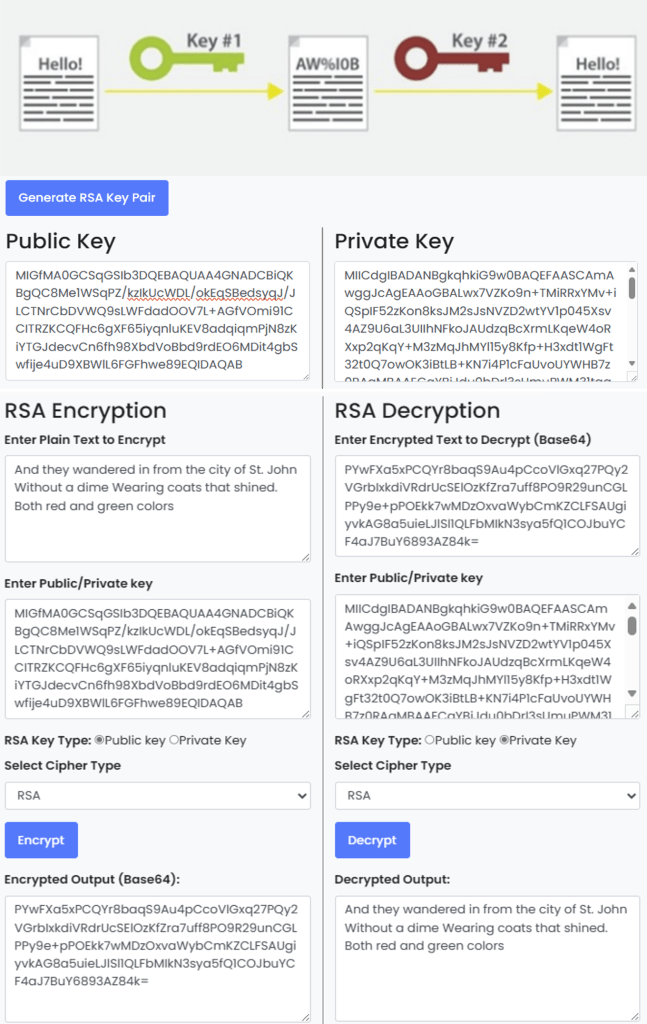
Building on the foundation of symmetric encryption, we now explore a revolutionary concept: public key cryptography. While symmetric encryption secured communication through shared secret keys, it presented a challenge – securely distributing them without interception. Public key cryptography eliminates this hurdle, introducing a powerful system of key pairs that enables secure communication between strangers.
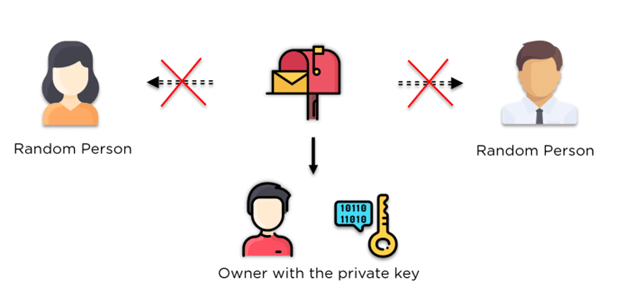
Securing Your Messages Online: The Role of Public Key Encryption
Imagine needing to send something very private over the internet. How can you ensure only the person you’re sending it to can read it? With more and more data leaks, keeping our online conversations safe is crucial. Public key encryption is a powerful tool that helps us do just that. It keeps our information safe in a world where digital security is often hard to come by.
Introduction to Public Key Cryptography
In the pioneering days of the digital era, specifically the mid-1970s, public key cryptography emerged as a transformative solution, redefining the approach to digital security. Unlike its predecessor, symmetric encryption, which uses a single key for encryption and decryption, public key cryptography introduces a dual-key system. This innovative system comprises public, openly shareable, and private keys, which the owner must keep secret. This breakthrough streamlined secure communication and elegantly addressed the once insurmountable challenge of secure key distribution.
Overcoming the Key Distribution Challenge
Symmetric encryption’s critical vulnerability lies in the encryption key’s secure transmission. The potential for interception made this a significant security concern. Public key cryptography ingeniously circumvents this issue by negating the need to exchange secret keys in advance, thus paving the way for secure communications between parties without prior direct contact.
Exploring the Asymmetry: Confidentiality and Authentication
The essence of public key cryptography lies in its asymmetric nature, utilizing key pairs that, while mathematically related, cannot be derived from one another. This foundational principle assures:
- Confidentiality, as messages encrypted with a public key, can only be decrypted by the corresponding private key, ensuring that only the intended recipient can access the message content.
- Authentication, where using a private key to sign messages allows the verification of the sender’s identity through the corresponding public key, affirming the message’s authenticity and integrity; this works like a digital passport – your private key acts as your stamp, and anyone with your public key can authenticate it from you, enhancing the trust in digital communications.
A Closer Look at the Core Algorithms
Innovative algorithms build the foundation of public key cryptography, enabling secure communication. Let’s explore some of the core algorithms and their unique strengths:
RSA (Rivest-Shamir-Adleman): Imagine you have a secret message you want to send to a friend. You lock the message in a box using a padlock that requires two keys to open – one key you share publicly and another that only your friend has. It is similar to how RSA works. It uses a pair of keys – a public key for encryption and a private key for decryption. RSA’s security relies on the fact that it is incredibly difficult to factor in large numbers, ensuring that only the intended recipient can unlock the message.
DSA (Digital Signature Algorithm): Think of DSA as a digital version of a handwritten signature. Just as a signature verifies the authenticity of a document, DSA verifies the authenticity of digital messages. It uses a pair of private keys to create a signature and a public key to confirm it. DSA’s security is based on the difficulty of solving the discrete logarithm problem, making it virtually impossible for anyone to forge a signature without the private key.
ECC (Elliptic Curve Cryptography): ECC is like a secret code that relies on the unique properties of elliptic curves. These curves have special mathematical properties that enable secure communication with smaller key sizes than other algorithms, making ECC particularly useful for mobile devices and other systems with limited computing power. The elliptic curve discrete logarithm problem, which is even more challenging to solve than the discrete logarithm problem used in DSA, provides security for ECC.
DH (Diffie-Hellman): Imagine you and a friend want to agree on a secret code to send messages, but you can only communicate through a public channel. DH allows you to establish this secret code securely, even if others can see your communication. In DH, both parties contribute to creating a shared secret, which they then use to encrypt and decrypt messages. DH’s security is based on the difficulty of solving the discrete logarithm problem, ensuring that eavesdroppers cannot determine the shared secret.
These core algorithms form the backbone of public key cryptography, enabling secure communication in various contexts. Many secure online transactions use RSA, while mobile devices and IoT systems often employ ECC. DSA is used for digital signatures, ensuring the authenticity and integrity of software downloads and digital documents. DH is a key component of secure protocols like HTTPS, providing a secure foundation for online communication.
By understanding the strengths and applications of these algorithms, we can better appreciate the critical role public key cryptography plays in our daily lives, keeping our digital interactions secure and private.
Addressing the Quantum Challenge
The cryptographic community faces a new challenge: quantum computing. Quantum computers can solve certain mathematical problems much faster than classical computers, threatening the security of existing public key cryptographic algorithms that rely on these problems for their security.
In July 2022, NIST announced the first group of quantum-resistant cryptographic algorithms for key establishment and digital signatures. Since the selection of four quantum-resistant algorithms, NIST and the cryptographic community have made significant progress, releasing draft standards for three and expecting finalization within the year, bringing us closer to the widespread adoption of this essential technology.
These new algorithms use mathematical problems, such as lattice-based cryptography, multivariate cryptography, and hash-based signatures, that both classical and quantum computers find difficult to solve. By adopting these quantum-resistant algorithms, the cryptographic community aims to ensure the security of public key cryptography and the integrity and confidentiality of digital communications in the face of future quantum computing advancements.
Hybrid Solutions for Optimal Efficiency
Public key cryptography offers significant security advantages but comes with a computational cost. Encryption and decryption operations using public key algorithms are generally slower than those using symmetric key algorithms. To achieve optimal efficiency without compromising security, cryptographers often employ a hybrid approach that combines the strengths of both public key and symmetric key cryptography.
In a hybrid system, a public key algorithm securely exchanges a shared secret key between communicating parties. This shared key is then used with a symmetric cipher, such as AES (Advanced Encryption Standard), to encrypt and decrypt the messages. The symmetric cipher efficiently handles the bulk of the data encryption and decryption, while the public key algorithm ensures the secure distribution of the symmetric key.
This hybrid approach offers several benefits:
- Enhanced security: The public key algorithm securely exchanges the symmetric key, protecting it from interception by unauthorized parties and maintaining the confidentiality of the communication channel.
- Improved performance: Symmetric ciphers are much faster than public key algorithms for encrypting and decrypting large amounts of data. The hybrid system performs better by using a symmetric cipher for most communication.
- Scalability: The hybrid approach allows for efficient communication with multiple parties. The public key algorithm can establish unique symmetric keys for each communication session, enabling secure and scalable communication networks.
Real-world examples of hybrid cryptographic systems include SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols, which secure web traffic, and PGP (Pretty Good Privacy) for email encryption. These systems demonstrate the effectiveness of combining public and symmetric key cryptography to create secure, fast, and scalable solutions.
As quantum computing advances, hybrid systems will likely incorporate quantum-resistant public key algorithms to maintain security. Organizations can ensure the long-term protection of their sensitive data and communications by staying at the forefront of cryptographic research and adopting hybrid solutions.
Conclusion: Empowering Individuals in the Digital Age
In an era where the digital world increasingly intertwines with our lives, we cannot overstate the importance of secure communication. Public key cryptography empowers individuals to take control of their online privacy and security. By understanding the fundamentals of this technology and its ongoing evolution, we can make informed decisions about protecting our sensitive information.
As we navigate the digital landscape, we must recognize that we all have a role in safeguarding our collective security. By embracing public key cryptography in our daily lives, whether through secure messaging apps, email encryption, or other privacy-enhancing tools, we contribute to building a more secure digital ecosystem.
Moreover, staying informed about the latest developments in cryptography, such as the ongoing efforts to develop quantum-resistant algorithms, allows us to remain proactive in the face of emerging threats. As individuals, we can advocate for the widespread adoption of these cutting-edge solutions, ensuring that our digital security remains resilient in the face of future challenges.
In a world where data breaches and cyber threats are too common, public key cryptography offers hope. It is a testament to human ingenuity, providing us with the tools to protect our digital lives and maintain our online interactions’ confidentiality, integrity, and authenticity. By embracing this technology and actively participating in its evolution, we secure our digital future and contribute to building a safer, more trustworthy digital world for all.
Looking ahead to the next in this blog series on cryptography
Public key cryptography’s ingenious use of key pairs has transformed the digital landscape, empowered secure communication, and solved the key distribution dilemma. However, its impact extends far beyond basic encryption. In the next blog, we’ll delve into the fascinating realm of digital signatures. We’ll uncover how this technology leverages public key cryptography to guarantee message authenticity and integrity, revolutionizing how we sign documents and verify identities in the digital world.
References
Wikipedia contributors. (n.d.). Public-key cryptography. Wikipedia. Retrieved from https://en.wikipedia.org/wiki/Public-key_cryptography.
Roberts, E. (n.d.). The problems with public-key cryptography. Stanford University. Retrieved from https://cs.stanford.edu/people/eroberts/courses/soco/projects/public-key-cryptography/probs.html.
IBM. (n.d.). Public key algorithms. IBM Documentation. Retrieved from https://www.ibm.com/docs/en/SSLTBW_2.1.0/com.ibm.zos.v2r1.icha700/icha700_Public_key_algorithms.htm.
Vallée, P. (n.d.). The societal impact of public key cryptography. Carleton University. Retrieved from https://people.scs.carleton.ca/~paulv/papers/society-impact-of-pkc-v4.pdf.
Encyclopaedia Britannica. (n.d.). Public-key cryptography. Britannica. Retrieved from https://www.britannica.com/topic/public-key-cryptography.
Oregon State University. (n.d.). Public key cryptography. Open Oregon State Education. Retrieved from https://open.oregonstate.education/defenddissent/chapter/public-key-cryptography/.
GeeksforGeeks. (n.d.). Public key encryption. Retrieved from https://www.geeksforgeeks.org/public-key-encryption/.
History Computer. (n.d.). Public key cryptography: A complete guide. Retrieved from https://history-computer.com/public-key-cryptography-complete-guide/.
Stack Exchange. (n.d.). Public signature of challenges as authentication. Crypto Stack Exchange. Retrieved from https://crypto.stackexchange.com/questions/89972/public-signature-of-challenges-as-authentication.
ScienceDirect. (n.d.). Public key algorithm. Retrieved from https://www.sciencedirect.com/topics/computer-science/public-key-algorithm.
TechTarget. (n.d.). Public Key Cryptography Standards (PKCS). SearchSecurity. Retrieved from https://www.techtarget.com/searchsecurity/definition/Public-Key-Cryptography-Standards.
Damian, M. (n.d.). Introduction to public-key cryptography. Villanova University. Retrieved from http://www.csc.villanova.edu/~mdamian/Past/csc3990fa08/csrs2007/01-pp1-7-MattBlumenthal.pdf.
University of California, Irvine. (n.d.). A history of public key cryptography. Retrieved from https://ics.uci.edu/~ics54/doc/security/pkhistory.html.
IBM. (n.d.). Overview of public key cryptography. IBM Documentation. Retrieved from https://www.ibm.com/docs/en/integration-bus/10.0?topic=overview-public-key-cryptography.
SSL Support Desk. (n.d.). Glossary: Public key cryptography. Retrieved from https://shop.sslsupportdesk.com/Support/glossary-public-key-cryptography.
HSC. (n.d.). Cryptography challenges posed by quantum computers. Retrieved from https://www.hsc.com/resources/blog/cryptography-challenges-posed-by-quantum-computers/.
IBM. (n.d.). Public key cryptography concepts. IBM Documentation. Retrieved from https://www.ibm.com/docs/en/ztpf/1.1.0.15?topic=concepts-public-key-cryptography.