
In the last blog on “The Ingenuity Behind Historical Ciphers,” we uncovered some of the earliest efforts to encrypt secret communication by hand. Today, we leap into the digital age to understand “Symmetric Key Encryption” – the revolutionary concept underpinning modern data security.
While historical ciphers relied on pen-and-paper techniques to scramble text, symmetric encryption uses computing power to convert messages into an encoded digital format that only intended recipients can decipher. It builds on the principles of its low-tech predecessors but executes them through automated algorithms on a sweeping scale across our digital infrastructure.
Secret Codes: The Role of Symmetric Cryptography in Modern Security
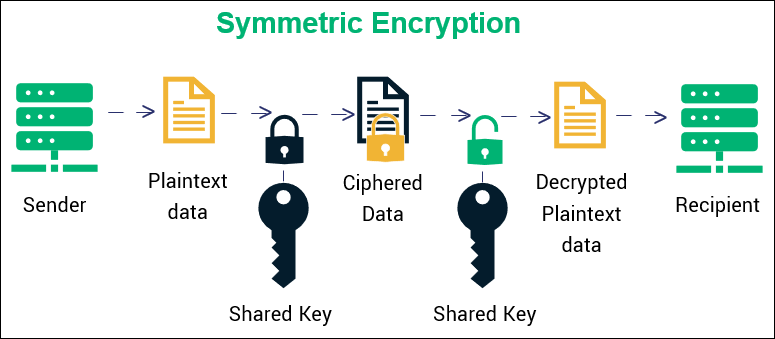
Symmetric cryptography allows two parties to communicate secretly using a shared private key. This single key scrambles and unscrambles messages, turning sensitive information into unreadable code. Symmetric encryption has protected important data for decades by developing special algorithms.
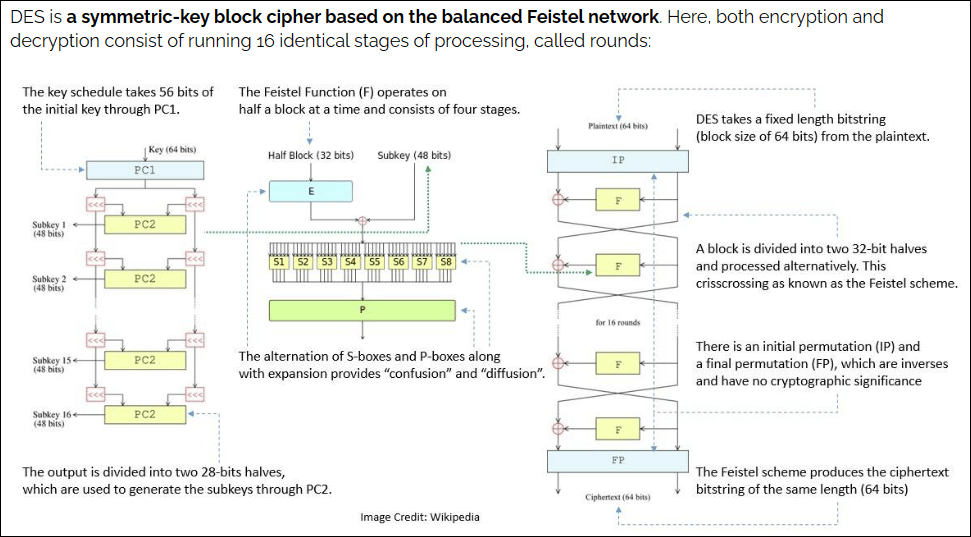
DES – The Origins of Modern Encryption
In the 1970s, the US government adopted the Data Encryption Standard (DES) algorithm created by IBM to encrypt sensitive but not top-secret information. DES was groundbreaking because it standardized encryption to safeguard confidential data. It used a 56-bit key and resisted attack for over 20 years before advances in computing posed a growing threat, leading to updated symmetric algorithms.
DES shielded bank data and government information before the internet era!
AES – Securing the Digital Age
As technology advanced, a new symmetric algorithm emerged – the Advanced Encryption Standard (AES) – which outperformed 15 competing ciphers to become the US standard by 2001 after a 5-year review. Picked for security, speed, and flexibility, AES uses 128, 192, or 256-bit keys to deliver strong electronic data transmission and storage protection. AES encrypts much of today’s digital communications, from online payments to classified documents.
AES has blocked all cracking attempts since 2001, guarding everything from your online shopping details to top-secret government files!
The Paradox of Symmetric Keys
Though symmetric cryptography enables fast, simple encryption using a shared private key, safely exchanging keys has risks. Hackers who steal the key while it is transmitted can access all communications! Modern methods use other encryption forms to prevent hackers from stealing the key and compromising all communications.
The Future of Symmetric Encryption
Despite key exchange challenges, symmetric cryptography provides the speed and scale required for widespread data encryption across banking, defense, and technology. As hacking attacks become more advanced, encryption like AES adapts to stay ahead, ensuring that cryptography remains society’s trusted protector in the digital age.
As we’ve seen, symmetric key encryption enabled immense leaps in digital data security – for a time. Eventually, cryptographers identified risks in symmetric key distribution. In the next blog on “Public Key Cryptography,” we’ll explore the revolutionary concept that solved this, pioneering new encryption and authentication techniques.
We’ll discover how public key cryptography removes risky key sharing through ingenious key pairs. We’ll learn how it enabled robust encryption across vast private networks, laying the groundwork for secure Internet communication.
We’ll also see how public key cryptography delivered watershed innovations like unforgeable digital signatures for identity verification, a fascinating real-life hack behind this cryptography revolution!