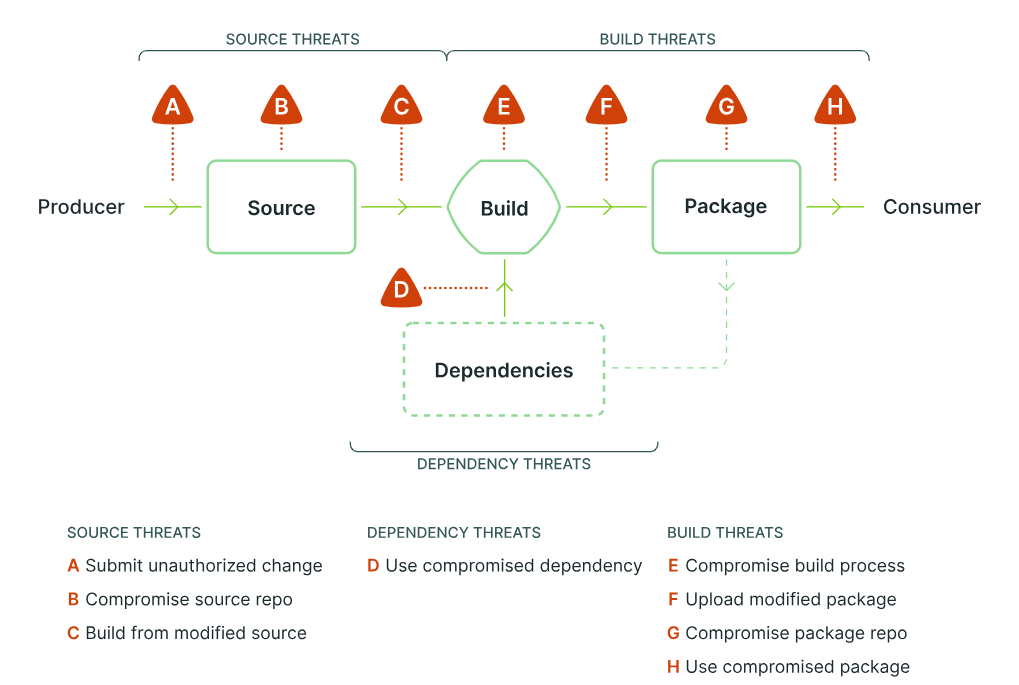
Introduction to SBOMs
A Software Bill of Materials (SBOM) is a comprehensive record of a software product’s components and dependencies. It provides vital information about the relationships between various software elements in the supply chain. SBOM assists organizations in managing dependencies, maintaining legal compliance, and reducing security risks.
Benefits of SBOMs
Utilizing a Software Bill of Materials (SBOM) offers organizations a variety of advantages, such as improved security within the supply chain. SBOMs provide visibility into the software supply chain, enabling organizations to identify potential security risks, licensing issues, and other problems before they cause significant damage. Additionally, SBOMs lead to better software management, allowing organizations to understand and manage the software components and dependencies throughout their supply chain, leading to more efficient administration and streamlined management. With an inventory of parts and dependencies, organizations can systematically check the list against databases of known vulnerabilities, proactively identify and address potential threats, and prioritize remediation efforts. SBOMs also document the licensing details of all components, ensuring organizations comply with open-source and proprietary license terms avoiding potential legal issues or penalties. By providing transparency into the software components and ensuring products perform securely and as intended, SBOMs can increase buyers’ confidence in consuming the software.
Challenges in SBOM Implementation
Implementing the Software Bill of Materials (SBOM) is facing various challenges. One of the biggest challenges is the need for widespread adoption, especially among open-source software, which makes it difficult for organizations to evaluate the risk associated with a product. Another challenge is the limited understanding and fear of exposure, which can hinder the industry’s adoption of SBOMs. Additionally, the need for clear standards for SBOM creation and transmittal creates confusion and hinders adoption. Balancing transparency with practical maintenance is essential for effective SBOM management. Several sources provide best practices and cases for using SBOMs to manage software cybersecurity risks.
Depth and Complexity
The depth of an SBOM refers to how far down the dependency tree it goes. Capturing direct dependencies is a good start, but going down to indirect dependencies provides fuller transparency. Striking the right balance between detail and complexity is crucial. An SBOM that only includes top-level components provides limited visibility, but going too deep can make SBOMs unwieldy to generate and manage.
Prioritization and Standard Formats
It is essential to prioritize critical components that carry higher risk or are poorly understood. Less necessary dependencies can be excluded or generalized for simplicity. Standard formats like CycloneDX and SPDX define required and optional fields to guide SBOM content, ensuring interoperability.
Use Cases and Updates
The level of detail required depends on the use case. An SBOM for internal software inventory can be high-level, while one for external consumption may require more comprehensive disclosure. Lastly, to ensure accuracy, you must manage updates to the SBOMs carefully, as they add complexity.
Regulatory Demands
U.S. and E.U. regulations demand the adoption of Software Bills of Materials (SBOMs) in supply chains to improve chain security, vulnerability management, and regulatory compliance. Standards and regulations are crucial in promoting the use of SBOMs, providing guidelines, promoting transparency, and ensuring compliance. Regulatory agencies and industry bodies, such as CISA and NTIA, recognize the importance of SBOM adoption and have initiated efforts to promote it across industries. These efforts help organizations manage risks in third-party software and enhance supply chain security.
Specific Regulations and Standards
Several regulations and standards influence supply chain software bills of materials (SBOMs). The U.S. Executive Order 14028 directs the National Institute of Standards and Technology (NIST) to develop guidelines for creating and publishing SBOMs and establish criteria for using them in federal procurement processes. Starting October 1, 2023, the Food and Drug Administration (FDA) will enforce the mandate that all medical devices running software must create and maintain an SBOM. The E.U. Cybersecurity Act (CRA) emphasizes the importance of SBOMs in software security and will significantly impact software vendors working in the E.U. market. These regulations promote transparency, ensure compliance, manage risks in third-party software, and enhance supply chain security. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recommends SBOMs as part of its guidelines for secure software development. Some industries that are required to use SBOMs due to regulations include medical devices and federal contractors.
Blockchain-Validated SBOMs
Requiring supply chain software providers to include a blockchain-validated Software Bill of Materials (SBOM) with each release can achieve numerous benefits. Blockchain technology ensures data security and immutability, making it challenging for malicious actors to tamper with the SBOM information and enhancing trust among supply chain stakeholders. Blockchain enables better traceability of software components and their dependencies, improving transparency across the entire software supply chain, which can help organizations identify potential risks and vulnerabilities more effectively. Blockchain can automate specific processes, such as the validation of SBOM information, through smart contracts, leading to increased efficiency and reduced costs associated with manual validation and verification. A blockchain-validated SBOM can help organizations demonstrate compliance with industry standards and regulations, as the information is securely stored and easily accessible for auditing purposes.
Blockchain in Supply Chain Management
Blockchain technology in supply chain management can improve transparency and efficiency. Organizations can identify potential risks and track the movement of goods and information using a software supply chain. Blockchain’s decentralized and tamper-evident ledger ensures secure storage and easy accessibility for auditing purposes, providing a single source of truth that is resistant to unauthorized modifications. Additionally, blockchain can improve collaboration and interoperability among supply chain stakeholders, leading to better decision-making and greater transparency. These benefits suggest that blockchain technology has the potential to revolutionize audit processes and accounting information quality.
Blockchain and Auditing
There are several ways in which the Bill of Materials (SBOM) can affect the auditing process within the supply chain. Blockchain technology ensures data immutability, making it difficult for malicious actors to tamper with the SBOM information. It guarantees the accuracy and reliability of the data used in the supply chain, which is essential for transparency during the auditing process. Blockchain technology allows for better traceability of software components and their dependencies, providing a transparent view of the entire software supply chain, aiding auditors in identifying potential risks and vulnerabilities more effectively, and tracking the movement of goods and information in the supply chain. Blockchain technology can affect all record-keeping processes, including how transactions are initiated, processed, authorized, recorded, and reported. Business model and process changes may impact back-office activities such as financial reporting and tax preparation, which can affect the auditing process.
Technical Aspects and Challenges
To understand the technical aspects of blockchain networks, such as distributed ledger technology, cryptographic algorithms, and consensus mechanisms, a different professional audit mindset and additional expertise will be necessary for digital transformations. The adoption of Software Bill of Materials (SBOM) faces several challenges, including limited understanding and fear of exposure, lack of widespread adoption, and difficulty for organizations to assess the risk posed by a product and undertake vulnerability evaluations.
Choosing Standardized Formats and Government Role
Choosing a widely accepted and standardized format for SBOMs is crucial to ensure consistency and ease of understanding. However, slow government action has hindered their adoption. The Office of Management and Budget has only made it optional for agencies to require SBOMs in federal I.T. contracts instead of mandating their inclusion. Another issue is the prevalence of low-quality SBOMs, leading organizations like CISA to prioritize SBOM quality improvements. To encourage their adoption, experts suggest that the government mandates their use by software suppliers to the U.S. government. Increasing SBOM production would shift the focus to SBOM consumption, which is essential for realizing the full benefits of SBOMs.
Overcoming Challenges
Using SBOMs in supply chains can be challenging, but organizations can overcome these challenges by focusing on several areas. The government should take a more active role in mandating the use of SBOMs, such as requiring their inclusion in federal I.T. contracts and software supplied to the government. Simplifying the SBOM creation and management process by integrating it into the development lifecycle, conducting pilot testing, and evaluating its ease of implementation, accuracy, and usefulness can streamline the process. Industry stakeholders, standards organizations, and government agencies should collaborate to establish a standardized and widely accepted format for SBOMs, ensuring consistency, interoperability, and ease of understanding. Standardizing SBOM generation and regeneration processes can help integrate SBOM creation into existing workflows and extract actionable insights from the SBOM data. Organizations should consider the benefits and challenges of using SBOMs, including their ability to tackle cybersecurity challenges.
Conclusion
Adopting software bills of materials (SBOMs) may be necessary to ensure supply chain security and compliance. The content and depth of an SBOM can vary depending on specific requirements and use cases, but there are guidelines and best practices to follow. An SBOM is a nested inventory of software components that provides critical information about the libraries, tools, and processes used to develop, build, and deploy a software artifact. Several resources exist to help with creating an SBOM. A proper Software Bill of Materials (SBOM) should contain unique identifiers and specify the dependencies between components. It must also include all top-level details and transitive dependencies or provide enough information for consumers to locate them. Choosing a standardized format like SPDX, CycloneDX, or SWID ensures consistency, interoperability, and easy comprehension. Suppliers must provide access control mechanisms for limiting SBOM data access to specific customers or users. The depth of an SBOM should align with an organization’s particular needs and use cases, with a more comprehensive SBOM providing better visibility into the software supply chain and effective risk and vulnerability management.
References
- https://fossa.com/blog/software-bill-of-materials-formats-use-cases-tools/
- https://www.techtarget.com/searchsecurity/post/The-benefits-and-challenges-of-SBOMs
- https://www.privacysense.net/terms/sbom/
- https://www.tripwire.com/state-of-security/sbom-security-fundamentals-and-best-practices
- https://www.scmagazine.com/brief/challenges-remain-in-sbom-adoption
- https://foresite.com/blog/software-bill-of-materials-sbom-basics/
- https://circleci.com/blog/what-is-a-software-bill-of-materials/
- https://onekey.com/blog/sbom/
- https://www.crowdstrike.com/cybersecurity-101/secops/software-bill-of-materials-sbom/
- https://scribesecurity.com/sbom/
- https://www.rezilion.com/blog/enhance-your-cybersecurity-with-an-sbom/
- https://fossa.com/blog/5-ways-sboms-can-strengthen-security/
- https://www.macsa.com/en/blog-en/benefits-of-blockchain-technology-in-supply-chain-traceability/
- https://www.synopsys.com/glossary/what-is-blockchain.html
- https://supplychaindigital.com/top10/top-10-uses-of-blockchain-in-supply-chain
- https://www.pivotpointsecurity.com/what-is-an-sbom-and-why-are-my-customers-suddenly-asking-for-one/
- https://www.analyticsinsight.net/5-benefits-of-blockchain-in-supply-chain-management/
- https://www.cisa.gov/sites/default/files/2023-04/sbom-sharing-lifecycle-report_508.pdf
- https://patents.justia.com/patent/20200201620
- https://edu.chainguard.dev/open-source/sbom/what-is-an-sbom/
- https://st.foundation
- https://www.harness.io/blog/software-bill-of-materials-sbom
- https://www.researchgate.net/publication/372136944_Trust_in_Software_Supply_Chains_Blockchain-Enabled_SBOM_and_the_AIBOM_Future
- https://www.ntia.doc.gov/files/ntia/publications/sbom_minimum_elements_report.pdf
- https://widgets.weforum.org/blockchain-toolkit/pdf/data-integrity.pdf
- https://www.sciencedirect.com/science/article/pii/S0925527323001950
- https://www.ibm.com/products/supply-chain-intelligence-suite/blockchain-transparent-supply
- https://arxiv.org/pdf/2307.02088.pdf
- https://101blockchains.com/blockchain-traceability/
- https://st.foundation
- https://publications.aaahq.org/jeta/article/19/2/105/174/Blockchain-s-Impact-on-Accounting-and-Auditing-A
- https://www.linkedin.com/pulse/auditing-blockchain-challenges-required-knowledge-high-level-wert
- https://www.researchgate.net/publication/356012393_Blockchain’s_Impact_on_Accounting_and_Auditing_A_Use_Case_on_Supply_Chain_Traceability
- https://www.sciencedirect.com/science/article/pii/S2772485922000606
- https://osf.io/uyb64/download
- https://www.ntia.gov/files/ntia/publications/minimum_elements_sbom_draft_20221027.pdf
- https://www.techtarget.com/searchsecurity/feature/The-benefits-and-challenges-of-adopting-SBOMs
- https://reversinglabs.com/blog/cisa-sbom-a-rama-tackles-challenges-5-key-takeaways/
- https://www.scmagazine.com/analysis/application-security/challenges-remain-in-sbom-adoption/
- https://fedscoop.com/sbom-roadblocks-adoption-software-supply-chain/
- https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2022/why-are-regulations-demanding-sbom-adoption
- https://finitestate.io/sbom-challenge-analysis-a-day-after/
- https://www.atlanticcouncil.org/blogs/new-atlanticist/using-sboms-software-accountability/