Table of Contents
- Introduction
- Project Planning
- Risk Assessment
- Security Policy
- Access Control Measures
- Data Encryption
- Network Security
- Employee Training
- Incident Response Preparation
- Security Monitoring
- Business Continuity
- Third-Party Risk Management
- External Audits
- Continual Improvement
- Staying Current on Security Trends
- Conclusion
- References
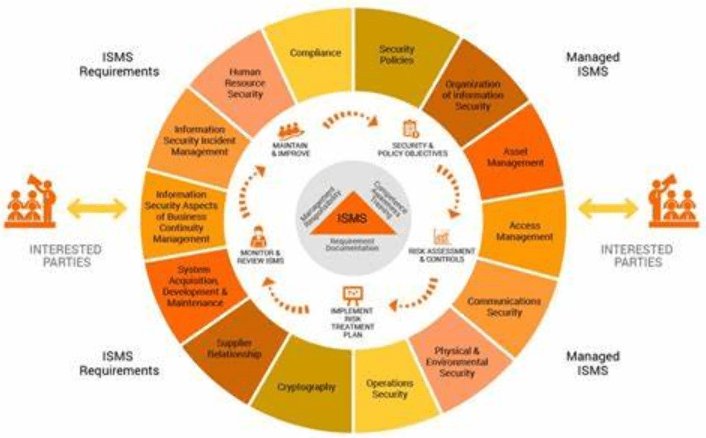
1. Introduction
This guide assists executive security leadership in developing a security and data protection program for organizations with enterprise architecture ranging from on-premises to hybrid cloud. This guide aligns with compliance frameworks, including ISO standards, HIPAA, ITAR, FedRAMP High, SOC2, PCI-DSS, and global privacy regulations. It covers essential components such as risk assessment, policy development, and incident response and provides practical tools like cost estimates, a team charter, and a RACI chart for implementation.
2. Project Planning
Objective
To develop an overarching master project plan that serves as the initial framework for the organization’s security and data protection program. This master plan will provide high-level estimates for budget, outline the preliminary team charter, introduce a RACI chart for role clarification, and offer an initial resource allocation strategy. It will also touch upon stakeholder communication, compliance frameworks, and technology stack alignment. Recognizing the complexity and multifaceted nature of the program, detailed subsidiary plans will be developed to elaborate on HR management, resource allocation, communication, budget, scope, and schedule, in alignment with PMP v7 guidelines.
Timeline
18-24 months
Budget
Total Estimated Budget: $2,000,000 – $2,500,000
- Risk Assessment: $200,000
- Security Policy: $100,000
- Access Control: $250,000
- Data Encryption: $150,000
- Network Security: $300,000
- Employee Training: $100,000
- Incident Response: $200,000
- Security Monitoring: $300,000
- Business Continuity: $200,000
- Third-Party Risk Management: $150,000
- External Audits: $100,000
- Continual Improvement: $150,000
- Staying Current: $50,000
Team Charter
The team will consist of experts in information security, risk management, compliance, and business continuity. The charter will outline roles, responsibilities, and the decision-making process.
RACI Chart
| Task/Role | Responsible | Accountable | Consulted | Informed |
|---|---|---|---|---|
| Risk Assessment | Risk Manager | CISO | Legal | CEO |
| Security Policy | Policy Team | CISO | Legal | COO |
| Access Control | Access Team | CISO | IT | CFO |
| Data Encryption | Crypto Team | CISO | IT | COO |
| Network Security | Network Team | CISO | IT | COO |
| Employee Training | HR | CISO | Legal | All Staff |
| Incident Response | IR Team | CISO | Legal | CEO |
| Security Monitoring | SOC Team | CISO | IT | COO |
| Business Continuity | BC Team | CISO | Legal | CEO |
| Third-Party Risk Management | Procurement | CISO | Legal | CFO |
| External Audits | Audit Team | CISO | Legal | CEO |
| Continual Improvement | CI Team | CISO | IT | COO |
| Staying Current | Research Team | CISO | IT | COO |
Resource Allocation
A detailed resource allocation plan will be developed, outlining the human, technological, and financial resources needed for each component of the program.
Stakeholder Communication
A communication plan will be developed to keep stakeholders informed and engaged throughout the program’s implementation.
Compliance Frameworks
HIPAA, ITAR, FedRAMP High, SOC2, PCI-DSS, and global privacy regulations.
Technology Stack
Hybrid cloud environment with 200 on-prem databases, Red Hat OpenShift, and SaaS, PaaS, and IaaS services running on AWS, GCP, Azure.
3. Risk Assessment
Inputs
Threat intelligence reports, previous audit findings, system architecture diagrams, and compliance requirements.
Processes
Utilize automated scanning tools and manual assessments to identify vulnerabilities. Conduct interviews with key personnel to understand the current risk landscape. Align findings with HIPAA, ITAR, FedRAMP High, and other compliance frameworks.
Outputs
A comprehensive risk assessment report that categorizes risks by severity, likelihood, and impact. This report will serve as the foundation for all subsequent security measures.
4. Security Policy
Inputs
Existing organizational policies, compliance requirements, and stakeholder input.
Processes
Drafting, reviewing, and finalizing the security policy document. This involves multiple rounds of internal reviews and legal consultations to ensure alignment with compliance frameworks.
Outputs
A finalized security policy document endorsed by leadership, which will be disseminated across the organization.
5. Access Control Measures
Inputs
User roles, system architecture, and data classification schema.
Processes
Implement role-based access controls, least privilege principles, and multi-factor authentication mechanisms. Validate these controls through periodic testing.
Outputs
A secure access control framework that minimizes unauthorized access and logs all access-related activities.
6. Data Encryption
Inputs
Data inventory, data classification levels, and technology stack.
Processes
Selection and implementation of encryption algorithms and key management systems. Regular audits to ensure encryption at rest, in transit, and in use.
Outputs
Encrypted data stores and a comprehensive key management policy.
7. Network Security
Inputs
Network architecture diagrams, firewall rules, and vulnerability assessment reports.
Processes
Network segmentation, firewall configuration, and continuous monitoring for unauthorized activities.
Outputs
A hardened network infrastructure with minimized vulnerabilities and a set of firewall rules.
8. Employee Training
Inputs
Employee roles, previous security incidents, and common threat vectors.
Processes
Develop and deliver training modules on phishing, social engineering, and secure password practices. Conduct simulated tests to measure effectiveness.
Outputs
Trained employees who are aware of their role in maintaining organizational security, and metrics on training effectiveness.
9. Incident Response Preparation
Inputs
Previous incident reports, current threat landscape, and organizational structure.
Processes
Develop incident response procedures, assign roles and responsibilities, and conduct regular drills to validate the plan.
Outputs
A thoroughly-tested incident response plan and a trained incident response team.
10. Security Monitoring
Inputs
Network logs, application logs, and system logs.
Processes
Utilize SIEM solutions to aggregate logs, set up alerts for abnormal activities, and conduct behavior analysis.
Outputs
Real-time monitoring dashboard, incident alerts, and periodic security reports.
11. Business Continuity
Inputs
Business process mapping, critical asset inventory, and risk assessment reports.
Processes
Develop and test a business continuity plan that includes data backups, alternative processing sites, and communication protocols.
Outputs
A validated business continuity plan and recovery time objectives (RTOs) and recovery point objectives (RPOs) for critical business processes.
12. Third-Party Risk Management
Inputs
Vendor contracts, service level agreements, and compliance requirements.
Processes
Conduct security audits and assessments of third-party vendors. Establish metrics for measuring vendor compliance.
Outputs
A vendor risk assessment report and a set of action items for non-compliant vendors.
13. External Audits
Inputs
All security policies, procedures, and compliance documentation.
Processes
Engage external auditors to validate the effectiveness of the security program. Address any non-compliance issues identified.
Outputs
External audit reports and a list of remediation actions for any identified gaps.
14. Continual Improvement
Inputs
Previous audit findings, current metrics, and stakeholder feedback.
Processes
Periodic internal audits and risk assessments to identify areas for improvement. Update policies and procedures based on findings.
Outputs
A list of improvements implemented, updated policies, and new security metrics.
15. Staying Current on Security Trends
Inputs
Industry reports, threat intelligence, and emerging technologies.
Processes
Attend security conferences, webinars, and workshops. Review and assess the applicability of new technologies and practices.
Outputs
A report summarizing key takeaways from conferences and recommendations for adopting new technologies or practices.
16. Conclusion
This security and data protection program is designed as a practical guide for CISOs in organizations with all combination of enterprise architectures. Aligned with ISO standards and multiple compliance frameworks, the plan outlines key components such as cost estimates, a team charter, and a RACI chart to clarify roles and responsibilities. It also includes metrics for each program element and a stakeholder communication strategy to foster transparency and governance across the organization
17. References
- https://www.databreachtoday.com/building-an-organizational-security-and-data-protection-guide-and-approach-a-14552
- https://www.ninjaone.com/blogposts/data-protection-plan-guide-8-steps-for-creation
- https://hrpp.berkeley.edu/sites/default/files/DataSecurity.pdf
- https://www.fortinet.com/content/dam/fortinet/assets/whitepaper/like-we-mean-it-it-security-policy-best-practices-guide.pdf
- https://resmo.com/blog/9-access-control-best-practices/
- https://www.dell.com/support/kbdoc/000177033
- https://www.iso.org/isoiec-27001-information-security.html
- https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html
- https://www.securiti.ai/itar-compliance/itar-regulations-employees
- https://info.spirion.com/blog/ten-steps-effective-data-protection-program
- https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-122.pdf
- https://www.esecurityplanet.com/network-security/it-security-policy-importance-best-practices/
- https://www.pdpc.gov.sg/-/media/Files/PDPC/PDF-Files/Resource-for-Organisation/PIMS-Guide-072016.pdf
- https://www.cpomagazine.com/cyber-security/iso-standards-for-information-and-data-protection/
- https://www.hhs.gov/hipaa/for-professionals/security/guidance/index.html
- https://www.virtru.com/blog/itar-compliance-checklist-for-data-protection/
- https://insights.sei.cmu.edu/insider-threat/2017/12/building-a-successful-data-protection-program.html
- https://www.techtarget.com/searchsecurity/definition/data-security
- https://www.techtarget.com/searchsecurity/tip/5-IT-security-policy-best-practices
- https://www.mastercard.us/en-us/merchants/safety-security/security-recommendations/site-data-protection-certification.html
- https://isms.online/iso-27701-privacy-information-management/
- https://www.hhs.gov/hipaa/for-professionals/guidance/index.html
- https://www.techtarget.com/searchcompliance/tip/Steps-for-building-a-privacy-program-plus-checklist
- https://www.cmu.edu/iso/governance/guidelines/data-protection.html
- https://www.bmc.com/blogs/security-policy-best-practices/