CMMI (Capability Maturity Model Integration) is a framework designed to help organizations enhance operational performance through a well-structured, process-oriented approach. It categorizes improvement into five distinct maturity levels, offering a clear pathway for organizational development. CMMI’s primary value lies in its practical application across various domains, enabling organizations to improve processes, drive efficiency, and innovate systematically. Its strength emerges when integrated with other standards, such as the ISO 27000 series, the Cybersecurity Framework (CSF), and the Center for Internet Security Controls (CIS). This integration fosters a holistic approach to excellence in organizational processes and cybersecurity, ensuring a comprehensive and effective strategy for achieving operational excellence and resilience against modern business challenges.
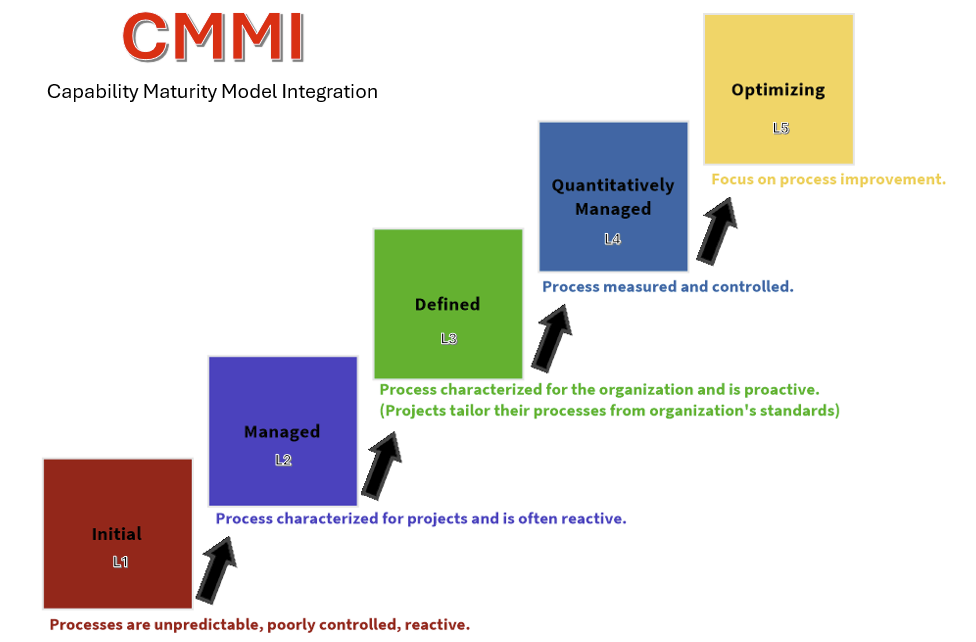
CMMI Maturity Levels:
A Journey of Continuous Improvement
- Initial (Level 1):
- At this foundational stage, processes are typically ad hoc. Success relies heavily on individual effort, and the organization needs more stable processes.
- Managed (Level 2):
- Processes are managed according to projects, emphasizing planning, execution, and monitoring. This level introduces basic project management practices, laying the groundwork for more consistent outcomes.
- Defined (Level 3):
- Processes are standardized across the organization and are characterized by documented standard processes, leading to more predictable outcomes, improved quality, and greater customer satisfaction.
- Quantitatively Managed (Level 4):
- Organizations implement quantitative methods to manage processes. The focus is on controlling processes through data analysis, ensuring predictability and effectiveness in achieving goals.
- Optimizing (Level 5):
- At the pinnacle of CMMI, organizations focus on continuous process improvement using incremental and innovative changes to enhance performance and meet business objectives.
Synergy with Other Standards:
I. ISO 27000 Series (ISO27K) Integration with CMMI
Process Improvement:
CMMI’s structured approach to process improvement complements the ISO27K series by providing a methodology for managing and enhancing processes related to information security management. While ISO27K sets the standards for information security, CMMI offers a pathway to achieving those standards through continuous process optimization.
- Risk Management:
- CMMI helps organizations identify, assess, and mitigate risks in a structured manner that complements ISO27K’s emphasis on risk assessment and treatment, making the risk management process more efficient and effective.
- Documentation and Standardization:
- By applying CMMI, organizations can standardize their documentation and procedures, a key requirement of ISO27K for achieving and maintaining certification.
Scenario – ISO 27000 series (ISO27K):
Implementing Access Control Improvements
Initial State:
A healthcare provider has basic access control policies per ISO27K requirements, such as requiring strong passwords and defining user roles. However, these policies are applied inconsistently across different departments, leading to potential security vulnerabilities.
Process Improvement with CMMI:
1. Assessment:
Using CMMI, the organization comprehensively assesses its current access control processes to identify inconsistencies and areas for improvement. This assessment includes evaluating the implementation of access controls across various departments and systems.
2. Goal Setting:
Following the assessment, the organization sets specific process improvement goals, including establishing uniform access control policies throughout all departments and adopting multi-factor authentication (MFA) to access sensitive patient data.
3. Plan and Implement Changes:
The organization develops a detailed plan to achieve improvement goals to achieve these goals, which includes:
- Standardizing access control policies to ensure consistency.
- Implementing MFA to add an extra layer of security.
- Training employees on the importance of these changes and how to comply with the new policies.
4. Measure and Optimize:
After implementing the changes, the organization measures the effectiveness of the new access control processes using CMMI’s structured approach, which could involve monitoring the number of unauthorized access attempts before and after implementing MFA. Based on this analysis, further optimization may be identified, such as enhancing user authentication methods or refining access levels.
Risk Management Enhancement:
- Structured Risk Assessment:
- The CMMI model guides the organization in conducting a structured risk assessment for access controls, identifying potential previously overlooked vulnerabilities.
- Mitigation Strategies:
- Based on the risk assessment, mitigation strategies are developed, such as implementing additional encryption for data accessed by remote employees.
- Documentation and Standardization:
- Following CMMI guidelines, the organization creates standardized documentation for the improved access control processes, including detailed policies, procedures, and training materials.
- Compliance with ISO27K:
- The standardized documentation and improved processes help demonstrate compliance with ISO27K requirements, facilitating the certification process.
Outcome:
By integrating CMMI’s structured approach to process improvement with ISO27K standards, the healthcare provider meets the compliance requirements and enhances its information security management system, leading to more efficient risk management, standardized documentation, and procedures, achieving higher security and operational excellence.
II. NIST Cybersecurity Framework (CSF) Enhancement through CMMI
- Roadmap for Maturity:
- CMMI provides a maturity model that guides organizations in systematically improving cybersecurity practices. This roadmap helps align with the CSF’s tiers, which describe the degree of sophistication and rigor of cybersecurity risk management practices.
- Performance Measurement:
- With CMMI, organizations can set clear goals for process improvement and measure their performance against these goals, supporting the CSF’s goal of ensuring that cybersecurity practices are implemented, effective, and continuously improved.
- Comprehensive Management:
- CMMI’s focus on process improvement across all organizational levels ensures that cybersecurity is integrated into the fabric of the organization’s operations, aligning with the holistic approach advocated by the CSF.
Scenario – NIST Cybersecurity Framework (CSF):
Enhancing Incident Response Capabilities:
Initial State:
- A financial services company has an incident response plan per CSF guidelines but struggles with slow reaction times and ineffective communication during cybersecurity incidents, impacting its ability to minimize damage.
Roadmap for Maturity with CMMI:
- Assessment and Goal Setting:
- The company uses CMMI to assess its current incident response processes, identifying areas of weakness, such as delayed breach detection and inefficient coordination among response teams. Based on this assessment sets clear goals for improvement, such as reducing detection time and improving team coordination.
- Plan and Implement Changes:
- To achieve these goals, the company plans and implements changes including:
- Integrating advanced threat detection tools to identify breaches more quickly.
- Establishing a dedicated incident response team with clear roles and responsibilities.
- Implementing regular, simulated cyber-attack exercises to improve team coordination and response times.
- Measure and Optimize:
- After implementing the changes, the company measures the effectiveness of its new incident response processes, which involves analyzing the time taken to detect and respond to incidents and evaluating the effectiveness of team coordination during these incidents. Based on this analysis, the company makes further optimizations, such as fine-tuning its threat detection tools and providing additional training to its response team.
Performance Measurement:
- Setting Performance Metrics:
- Using CMMI, the company establishes clear metrics to measure the performance of its incident response processes, such as mean time to detect (MTTD) and mean time to respond (MTTR) to incidents.
- Continuous Improvement:
- The company uses these metrics to continuously monitor and improve its incident response capabilities, aligning with the CSF’s emphasis on effective and constantly improved cybersecurity practices.
Comprehensive Management:
- Integrating Across Levels:
- Applying CMMI principles, the company ensures that improvements in incident response are integrated across all levels of the organization, from the executive team to the IT department, including regular updates to the executive team on cybersecurity risks and incident response readiness.
- Holistic Approach:
- By focusing on process improvement across the organization, the company aligns with the CSF’s holistic approach to cybersecurity, ensuring that incident response is a technical function and part of the organization’s overall risk management strategy.
Outcome:
By applying CMMI’s structured approach to process improvement, the financial services company enhances its incident response capabilities in alignment with the CSF. This results in quicker detection of cybersecurity incidents, more efficient response times, and better coordination among response teams. By setting clear performance metrics and aiming for continuous improvement, the company ensures its cybersecurity practices are effective and capable of evolving with the changing threat landscape. This comprehensive management of cybersecurity risks significantly improves the organization’s resilience against cyber threats, demonstrating the value of integrating CMMI with the Cybersecurity Framework.
III. Center for Internet Security Controls (CIS) and CMMI
- Systematic Application of Controls:
- Implementing CMMI can help organizations in the structured application of CIS controls by ensuring that the processes related to cybersecurity are not only defined but are also consistently managed and optimized.
- Benchmarking and Optimization:
- CMMI’s emphasis on benchmarking and continuous improvement can enhance the effectiveness of CIS controls. Through CMMI, organizations can evaluate the efficiency of the CIS controls they have implemented, identify areas of improvement, and systematically optimize their security posture.
- Integration Across Processes:
- CMMI promotes the integration of cybersecurity controls into broader business processes. This holistic approach ensures that CIS controls are not implemented in isolation but are part of an integrated system of processes, enhancing overall security and operational efficiency.
Scenario – Center for Internet Security (CIS):
Implementing Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
Initial State:
- A technology startup has adopted CIS Control 5 (Secure Configuration for Hardware and Software) but faces challenges in consistently applying secure configurations across mobile devices, laptops, workstations, and servers. Configurations are often manually set, leading to consistency and security gaps.
Systematic Application of Controls with CMMI:
1. Assessment and Standardization:
Applying CMMI, the company starts with a comprehensive assessment of its current hardware and software configurations. It identifies variations in configurations across devices and servers that could lead to vulnerabilities.
2. Goal Setting for Secure Configuration:
The company establishes clear goals to achieve consistent, secure configurations across all devices, in line with CIS Control 5. These goals include standardizing security settings by turning off unnecessary ports and services and ensuring the application of the latest software updates.
3. Implementing Process Changes:
The company develops a process for automatically deploying secure configurations to all devices and servers to meet these goals involves:
- Selecting configuration management tools that can automate the deployment of secure settings.
- Creating a centralized repository of approved configurations that meet CIS benchmarks.
- Training IT staff on the new tools and processes to ensure proper implementation and maintenance.
4. Continuous Improvement and Benchmarking:
With the process in place, the company continuously monitors the effectiveness of its secure configurations, using CMMI’s benchmarking principles, including regular audits to ensure configurations remain in compliance with CIS benchmarks and identify any deviations or new vulnerabilities.
Benchmarking and Optimization:
- Performance Metrics:
- The company establishes performance metrics to evaluate the effectiveness of its secure configurations, such as the percentage of devices compliant with the standard configurations and the time taken to update configurations in response to new vulnerabilities.
- Optimization:
- Based on these metrics, the company regularly reviews and optimizes its configuration management processes, ensuring they remain efficient and effective in maintaining security standards.
Integration Across Processes:
- Cross-Functional Collaboration:
- Leveraging CMMI, the company integrates secure configuration processes with other business operations, ensuring that cybersecurity is considered in product development, customer support, and HR processes (for managing employee devices).
- Holistic Security Culture:
- This approach fosters a security culture across the company. CIS controls are not just IT responsibilities but are integrated into the broader operational ethos, enhancing overall security and operational efficiency.
Outcome:
By applying CMMI principles to the implementation of CIS Control 5, the technology startup achieves a systematic and optimized approach to secure configurations across its hardware and software. This structured application and continuous improvement of CIS controls, integrated into the company’s broader business processes, not only enhance the security posture but also contribute to operational efficiency and resilience against cyber threats.
Conclusion:
The Art of Mastery in Process Improvement
Implementing CMMI alongside standards like ISO27K, CSF, and CIS marks a strategic approach to process improvement and cybersecurity management. The combination enhances organizational maturity and efficiency and fosters a culture prioritizing innovation and resilience, providing a competitive advantage in today’s business and cybersecurity environment. CMMI is a practical tool that steers organizations toward sustainable growth, improved performance, and robust security measures.
A CMMI maturity objective gap assessment facilitates continuous improvement and compliance with international standards, offering organizations a clear and actionable strategy for achieving operational excellence in a dynamic global landscape.
References:
- CMMI Institute website: (https://cmmiinstitute.com/) The official source for all things CMMI.