Summary
While ad hoc responses to security incidents are sometimes unavoidable, a systematic approach to managing information risks is essential. This guide provides actionable insights by fusing the wisdom from ISO 27001:2022 and NIST 800-30, 800-37, and 800-39 standards. The goal is to help organizations avoid or mitigate the adverse impacts of security incidents.
Leadership and Governance: Setting the Tone at the Top
ISO 27001:2022, Clause 5 & NIST 800-39
- Inputs: Senior leadership buy-in, organizational structure, and existing governance frameworks.
- Process: Establish a governance structure that includes roles, responsibilities, and reporting lines.
- Output: A governance model and a culture that values security.
- Actionable Guidance: Senior leadership must be actively involved in risk management. Establish a governance structure that includes roles, responsibilities, and reporting lines. This sets the tone for a culture that values security.
Establish Context and Scope for Risk Assessment
ISO 27001:2022, Clause 4 & NIST 800-30
- Inputs: Organizational objectives, existing ISMS scope, and asset inventory.
- Process: Define the scope of your ISMS, including all information the organization owns, depends upon, or is responsible for.
- Output: A clearly defined ISMS scope and risk assessment context.
- Actionable Guidance: Define the scope of your ISMS. Prioritize significant risks and allocate resources accordingly.
Additional Note: The scope should align with your business objectives and be communicated clearly to all stakeholders.
Identifying Viable Information Risks
ISO 27001:2022, Annex A & NIST 800-30
- Inputs: Historical incident data, stakeholder insights, and asset inventory.
- Process: Use data analysis and creative thinking to identify risks.
- Output: A list of identified and shortlisted risks.
- Actionable Guidance: Use brainstorming sessions with relevant stakeholders to generate a list of potential risks. Use rational criteria to shortlist the most viable ones.
Additional Note: Consider using industry benchmarks and threat intelligence feeds to enrich your risk identification process.
Risk Analysis: The Objective and Subjective Lens
ISO 27001:2022, Clause 6 & NIST 800-30
- Inputs: Identified risks, historical data, and expert opinions.
- Process: Use both objective and subjective approaches for risk analysis.
- Output: A comprehensive risk analysis report.
- Actionable Guidance: Use both objective and subjective approaches for risk analysis. Both are essential for a balanced view of risks.
Additional Note: Leverage tools and frameworks like FAIR for quantitative risk analysis where applicable.
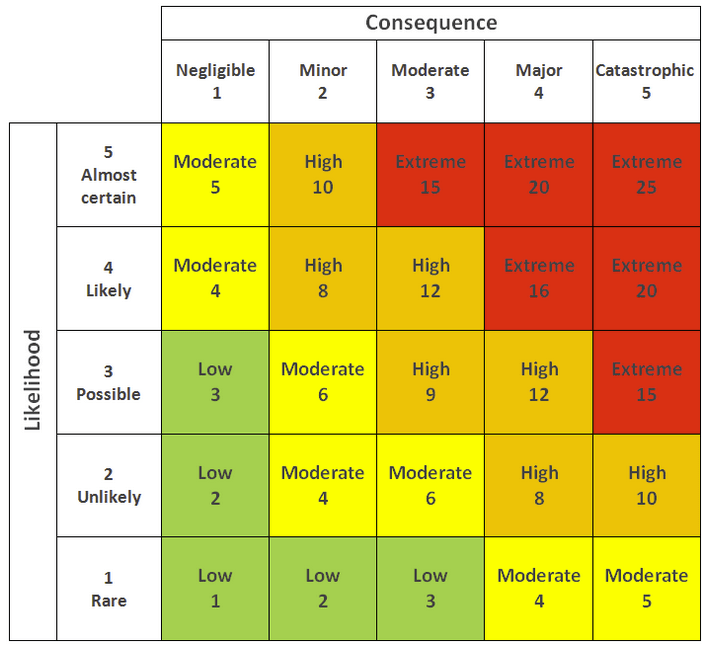
Evaluating Risks: The Art of Prioritization
ISO 27001:2022, Clause 8 & NIST 800-37
- Inputs: Risk analysis report, business objectives, and stakeholder input.
- Process: Use tools like the Probability Impact Graphic (PIG) to evaluate risks.
- Output: A prioritized list of risks.
- Actionable Guidance: Use tools like the PIG to evaluate and prioritize risks relative to each other.
Additional Note: Involve business unit leaders in the risk evaluation process to align it with business objectives.
Deciding on and Initiating Risk Treatments
ISO 27001:2022, Annex A & NIST 800-39
- Inputs: Prioritized list of risks, existing controls, and resource availability.
- Process: Decide on appropriate risk treatments based on priority.
- Output: A Risk Treatment Plan.
- Actionable Guidance: Risks in the red zone on the PIG should be treated as high-priority. Consider grouping similar risks together for more efficient treatment.
Additional Note: Always consider the cost-benefit analysis when deciding on risk treatments.
Risk Treatment Options: The Four Pillars
ISO 27001:2022, Clause 6 & NIST 800-39
- Inputs: Risk Treatment Plan, organizational policies, and stakeholder input.
- Process: Implement chosen risk treatments.
- Output: Implemented controls and mitigations.
- Actionable Guidance: Implement the four pillars of risk treatment: Avoid, Share, Mitigate, and Accept the risk.
Additional Note: Ensure that your risk treatment options are compliant with legal and regulatory requirements.
Communication: The Heartbeat of Risk Management
ISO 27001:2022, Clause 7 & NIST 800-37
- Inputs: Risk Treatment Plan, stakeholder list, and communication channels.
- Process: Inform all stakeholders about the risk landscape and chosen treatments.
- Output: Informed and engaged stakeholders.
- Actionable Guidance: Keep all stakeholders informed about the risk landscape and the chosen treatments.
Additional Note: Use multiple channels of communication, including meetings, newsletters, and dashboards, to keep stakeholders informed.
Monitoring and Review: The Cycle of Improvement
ISO 27001:2022, Clause 9 & NIST 800-39
- Inputs: Implemented controls, incident reports, and change logs.
- Process: Continuously monitor the risk landscape for changes.
- Output: Updated risk assessments and treatment plans.
- Actionable Guidance: Monitor the risk landscape for changes, including new threats and vulnerabilities. Use these insights to loop back into your risk management process for ongoing improvement.
Additional Note: Regular audits and third-party assessments can provide valuable insights into the effectiveness of your risk management program.
Organizations can build a robust yet flexible risk management program aligned with ISO and NIST standards, providing a practical, actionable path forward.