
Title: The Data Security Posture Management Show: A Podcast-style Exploration of IBM Guardium Insights SaaS – DSPM
Podcast Outline: “Data Security Deep Dive: IBM Guardium Insights SaaS DSPM”
Host: Jim is an experienced podcast emcee and passionate about tech journalism.
Expert Guest: Alex Johnson, Chief Information Security Officer at CloudSecure Inc., specializing in hybrid cloud-native architectures with data sources in AWS, GCP, Azure, and SaaS apps like SharePoint, Slack, and Google Drive.
Format: Interview and Q&A sessions with commercial breaks.
Introduction [0:00-2:00]
- Jim: “Hello, listeners! Welcome to the ‘Data Security Podcast.’ I’m Jim, your tech journalist host with years of experience demystifying complex tech topics. Today, we’re diving into IBM Guardium Insights SaaS DSPM, an innovative solution in cloud data security. This platform is a game-changer for managing your cloud and SaaS accounts’ data security posture. We’ll explore how it revolutionizes data security, compliance, and risk management, making it simpler yet more effective. Expect practical insights and expert opinions on making the most of this tool. So, stay tuned, share your questions or experiences, and let’s embark on this enlightening journey into the IBM Guardium Insights SaaS DSPM world together!”
- Jim: “IBM Security’s IBM Guardium Insights, a cloud-native Data Security Posture Management (DSPM) solution, is a comprehensive tool for managing data security in cloud environments and SaaS applications. This platform provides security and compliance teams complete visibility and control over sensitive data. It excels in automating the inventory and discovery of sensitive data, tracking data movement, and identifying unusual access patterns to prevent breaches. Seamless integration with leading data stores on AWS, Azure, and GCP and its cloud-native, agentless deployment make IBM Guardium Insights DSPM indispensable for modern businesses prioritizing data security.”
- Jim: “Data security in cloud environments is crucial in today’s digital landscape. Cloud computing, a backbone of modern business operations, handles sensitive customer information and intellectual property. However, its shared and virtual nature introduces specific security challenges. As remote work and SaaS applications become more prevalent, implementing robust security measures is essential to prevent data breaches, preserve customer trust, and comply with regulations. IBM Guardium Insights DSPM addresses these challenges, offering vital tools to protect data in the dynamic cloud environment.”
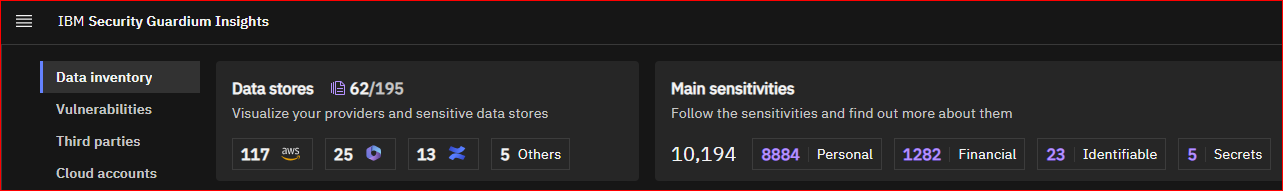
Figure 1: GI-SaaS DSPM Overview Screen. This image displays the main interface of the GI-SaaS Data Security Posture Management (DSPM) system.
Segment 1: Overview of DSPM [2:00-10:00]
- Jim: Today, we’re thrilled to welcome Alex Johnson to our show. As the Chief Information Security Officer (CISO) of CloudSecure Inc., a renowned global leader in cloud security and an esteemed IBM partner, Alex has played a pivotal role in advancing cloud data security. His leadership has steered CloudSecure Inc. to significant achievements in this domain. Alex, we’re inspired by your work with IBM Guardium Insights SaaS DSPM. Could you share your journey in this field with us and how it has influenced your approach to data security?
- Alex: “Thanks, Jim. Navigating the evolving landscape of cloud security has indeed been fascinating. At CloudSecure Inc., we’ve realized the importance of robust data security strategies, particularly for managing sensitive data across diverse cloud platforms. In this context, Guardium Insights SaaS DSPM has been a key asset, providing us with the essential tools to ensure data security and compliance.”
- Jim: “Alex, I understand you’ve had significant experiences with GDPR transborder data flows using IBM GI-SaaS DSPM, a hot topic for many of our listeners, especially considering the stringent regulations around data transfer in and out of the EU. Could you share a bit about your journey in this area and how these experiences have shaped your approach to data security?”
- Alex: “Certainly, Jim. There was a notable incident with one of our clients. They were about to inadvertently transfer sensitive data from an AWS region in the EU to the United States and this could have resulted in a significant GDPR violation. Fortunately, we used IBM Guardium Insights SaaS DSPM, which flagged this potential transfer. Our team was alerted in time, and we prevented the data movement before any violation occurred. It was a clear demonstration of how critical DSPM is in tracking and controlling data flow, especially for Personally Identifiable Information (PII) outside the European Union (EU).”
- Jim: “That’s a powerful example of GI-SaaS DSPM in action. It’s not just about detecting threats but also about preventing regulatory missteps. Thanks for sharing that, Alex.”
- Jim: “Alex, for our listeners who may be new to this, could you give us an overview of GI-SaaS DSPM and why it’s becoming increasingly vital?”
- Alex: “Absolutely, Jim. IBM’s GI-SaaS DSPM is about managing and securing an organization’s cloud-native data. It’s a process that involves continuous monitoring, analyzing data security controls, and identifying vulnerabilities. In today’s multi-cloud and SaaS-dominated environment, GI-SaaS DSPM is crucial. It automates data inventory and enables real-time monitoring of sensitive data, vital for identifying risks and ensuring compliance.”
- Jim: “I’ve heard you speak of the term’ shadow data’ and how it’s a growing concern. First, what is ‘shadow data?’ How significant is this issue, and how does GI-SaaS DSPM help?”
- Alex: “Shadow data, Jim, is like the digital equivalent of items lost in your attic. It’s there, but often out of sight and mind. In the digital world, this means unmonitored and unsecured data lurking in unauthorized places, posing real risks to security and compliance. IBM’s GI-SaaS DSPM steps in as a skilled detective. It finds and classifies this elusive data, tracks its movements, and shores up defenses. Essentially, it’s about turning these hidden corners into well-lit, secure spaces, reducing risks and ensuring compliance.”
- Jim: “Intriguing! It sounds like GI-SaaS DSPM is a game-changer in tackling these modern challenges. Let’s take a moment to hear more about DSPM from IBM’s perspective. We’ll be back shortly with more insights from Alex.”
- Commercial Break From IBM: What is DSPM? (1 minute)
Segment 2: Deep Dive into IBM Guardium Insights SaaS DSPM Features [10:00-20:00]
- Jim: “Welcome back, folks! We just heard some fascinating insights from IBM about Data Security Posture Management. With such sophisticated solutions at hand, it’s clear why experts like Alex are vital in navigating these complex data landscapes. Now, Alex, let’s dive deeper into IBM Guardium Insights SaaS DSPM. Could you walk us through its key features and how they empower organizations in their data security efforts?”
- Alex: “Absolutely, Jim. The key features of IBM Guardium Insights SaaS DSPM include:”
- Automated Data Inventory and Discovery: The solution provides automated data inventory and discovers data in known and shadow data stores. It identifies and classifies sensitive data in cloud workloads and SaaS applications, enabling organizations to gain complete visibility of their data.
- Data Movement Tracking: Guardium Insights SaaS DSPM tracks the actual (has occurred) and potential (can, has not yet occurred) data movement. Flagging anomalous data access and movements helps prevent data leakage and compliance violations.
- Active Remediations of Data Security Vulnerabilities: The solution offers remediation guidance for all identified data security vulnerabilities, with optional active remediation specifically for critical ones, enabling organizations to address security issues and strengthen their data posture proactively.
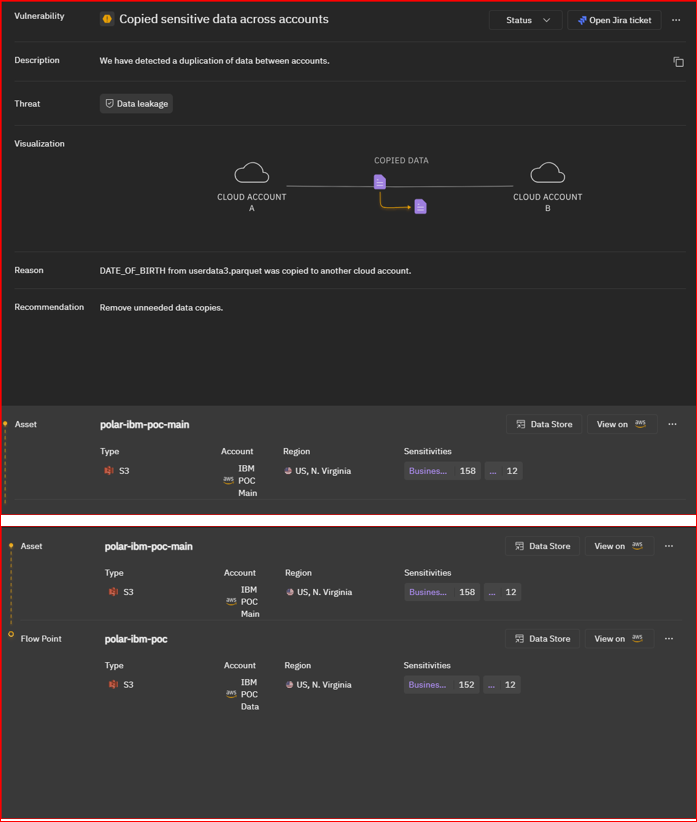
Figure 2: illustrates the identification of unauthorized data duplication across cloud accounts, explicitly highlighting the copying of sensitive ‘DATE_OF_BIRTH’ information from ‘userdata3.parquet’ to another account. The graphic also includes a recommendation for remediation: removal of unnecessary data copies to mitigate the security risk.
- Alex: “continuing”
- IBM Guardium Insights SaaS DSPM effectively integrates with the most popular data sources across major public clouds. It features compatibility with Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), and various widely used SaaS applications, including Google Drive, Slack, and Microsoft 365. This compatibility ensures organizations can efficiently analyze their data inventory vulnerabilities across these platforms, streamlining analysis that would otherwise be practically difficult.
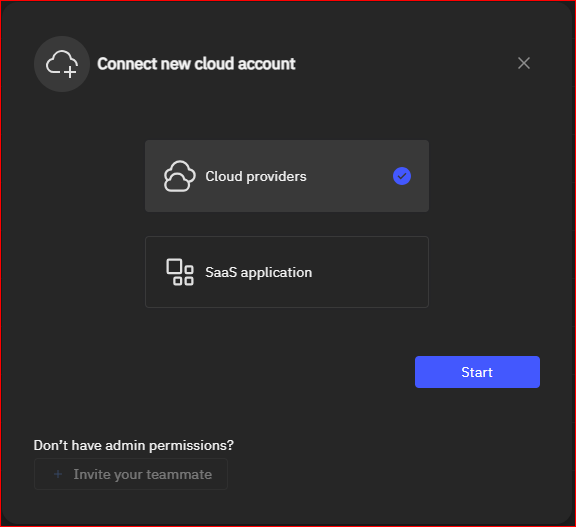
Figure 3: Adding Cloud Accounts and SaaS Applications. This graphic illustrates the straightforward method for selecting and adding cloud accounts and SaaS applications.
- Alex: “continuing ”
- Agentless Deployment: As a SaaS-native solution, IBM Guardium Insights SaaS DSPM deploys without agents, eliminating any performance impact on crucial business applications. The scanning process is swift, takes only minutes, and starts to populate the results and sensitive data inventory in short order.
- Extensive Support for Different Data Environments: Guardium Insights SaaS DSPM supports many data environments, including cloud workloads and SaaS applications. It offers comprehensive support for AWS, Azure, GCP, file formats, and database engines, enabling organizations to tailor their data security and compliance reporting to cloud needs.
- Alex: “Overall, IBM Guardium Insights SaaS DSPM provides organizations with comprehensive visibility, control, and remediation capabilities for ensuring data security and compliance in cloud environments.”
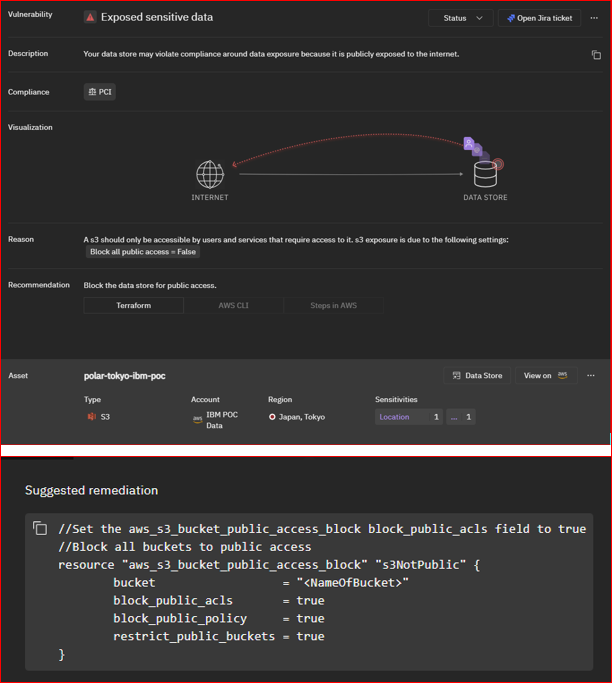
Figure 4: Sensitive Data Exposure Alert – GI-SaaS DSPM detects a data vulnerability where sensitive data is publicly exposed online, potentially violating PCI compliance. The S3 configuration allows public access, which is the cause of the vulnerability. The provided Terraform script suggests remediation to secure the S3 bucket by blocking public access.
- Jim: “Alex, how does DSPM address data sprawl, unknown data, and compliance?”
- Alex: “Jim, let’s take these one at a time, starting with data sprawl. DSPM helps organizations tackle data sprawl by providing automated data inventory and discovery capabilities. It identifies and classifies sensitive data in known and shadow data stores, allowing organizations to gain visibility into their data landscape, including data stored in various cloud workloads and SaaS applications. Organizations can better manage and secure their data assets by understanding where sensitive data resides.”
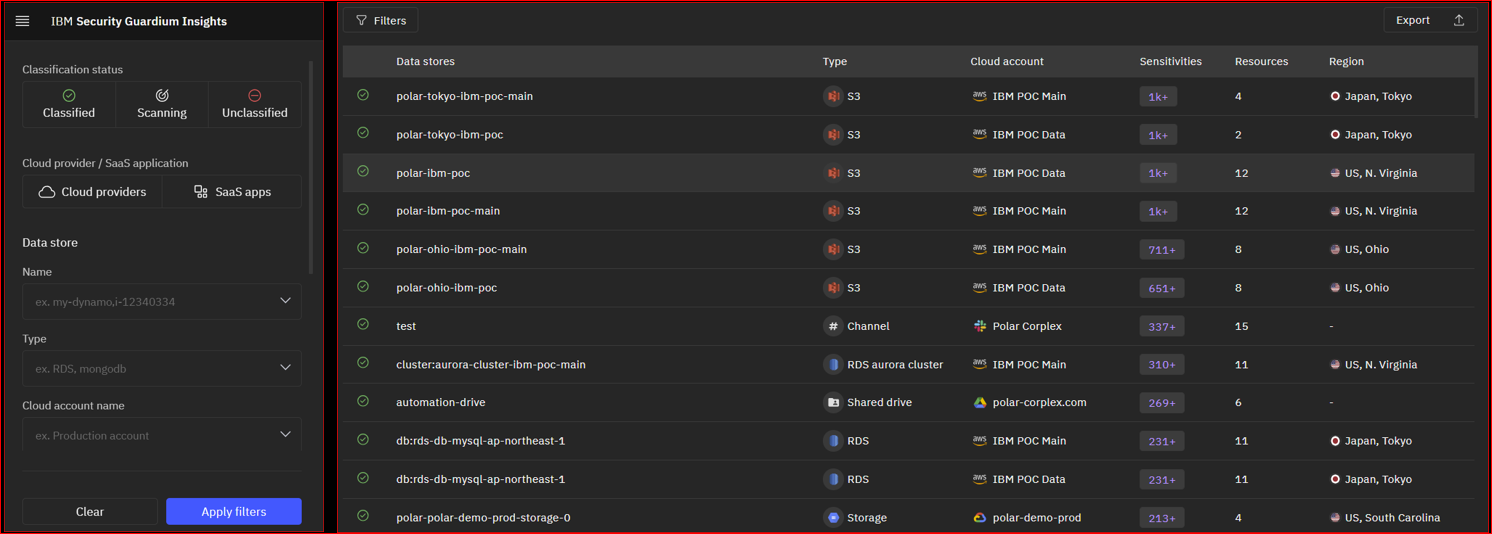
Figure 5: Inventory of Discovered and Classified Sensitive Data in GI-SaaS DSPM. This figure showcases a portion of identified cloud account sensitive data inventory and filters.
- Alex: “Let’s delve into handling ‘unknown’ or ‘shadow’ data with GI-SaaS DSPM. This term describes data within an organization’s environment requiring active management. IBM’s DSPM plays a crucial role here by continually monitoring data movement across the organization. It’s adept at tracking actual and potential data movements, highlighting unusual or unauthorized access patterns. Such vigilance allows us to spot and flag any suspicious activities promptly. This proactive approach is key in initiating timely investigations and taking necessary steps to secure data, keeping those unknown data elements in check.”
- Alex: “Maintaining compliance with data security regulations is vital for any organization. GI-SaaS DSPM supports this by offering insights for managing data security posture and identifying vulnerabilities. It proactively provides solutions to address these issues, helping organizations stay compliant with regulations. GI-SaaS DSPM ensures that only authorized personnel can access sensitive data, which prevents unauthorized use and data breaches. Additionally, its integration with popular cloud platforms like AWS, Azure, GCP, and various SaaS applications makes data access and analysis more efficient. This integration streamlines the compliance reporting process, saving time and effort for security teams.”
- Alex: “In summary, GI-SaaS DSPM helps organizations address data sprawl by providing inventory and discovery capabilities, tracking unknown data through continuous data movement, and ensuring compliance by identifying vulnerabilities and enabling active remediations.”
- Jim: “Speaking of data sprawl, I read an interesting case where a company found critical data in unexpected cloud storage. It’s like finding a hidden treasure in your backyard! Does this ring a bell in your experiences, Alex?”
- Alex: “It’s more common than you think, Jim. That’s why a comprehensive solution like GI-SaaS DSPM is key to uncovering and securing these ‘hidden treasures.’”
- Jim: “That’s a great point, Alex. It’s remarkable how frequently valuable data gets overlooked amid the vast expanse of cloud storage. We’ve just heard that having the right tools to unearth and secure these hidden data assets is crucial. Speaking of insights and leadership in data security, let’s hear what industry analyst EMA says about IBM’s role in shaping this field with their DSPM solutions. Stay with us for a quick message from EMA.”
- Commercial Break From EMA: Industry analyst EMA writes that ‘IBM has solidified its position as a leader in data security with DSPM (1 minute)
Segment 3: Listener Call-In Questions [20:00-30:00]
- Jim: “Thanks for sticking with us on the ‘Data Security Podcast.’ As highlighted by EMA, IBM’s position in data security indeed shows the importance of solutions like Guardium Insights SaaS DSPM. Now, let’s turn the mic over to you, our listeners. We’re opening the lines for your questions, allowing you to have your inquiries answered by our expert, Alex Johnson.
- Jim: “Let’s dive in. Good morning, Rob. You’re our first caller today. What question do you have for Alex?”
- Rob: “Hi, what percentage of organizations store sensitive data in multiple cloud providers?”
- Alex: “Rob, that’s a great question. Recent studies indicate that approximately 77% of organizations store sensitive data across multiple cloud providers. Alarmingly, 63% acknowledge the potential or actual exposure of sensitive data in the cloud. Furthermore, 42% of these organizations need to be made aware of the exact location of their sensitive data, often referred to as ‘Shadow data.’ This uncertainty, combined with the inherent complexities of securing public cloud configurations, contributes significantly to the fact that 45% of data breaches occur in the cloud, underscoring the need for robust cloud security measures.”
- Jim: “Next, we have Sarah on the line. Sarah, your question?”
- Sarah: “How does Guardium Insights SaaS DSPM address data sprawl and unknown data?”
- Alex: “Sarah, it tackles this by offering cloud data visibility, analyzing data movement, and providing robust data protection. It’s a holistic approach to managing cloud data sprawl.”
- Jim: “Michael, you’re up. What do you want to know?”
- Michael: “What risks related to data security and privacy does Guardium Insights SaaS DSPM mitigate?”
- Alex: “Michael, it’s designed to mitigate various risks, including exposure of PCI records, PII leaks, plaintext password sharing, GDPR compliance violations, and data leakage to third parties connected to your cloud account. It’s quite comprehensive.”
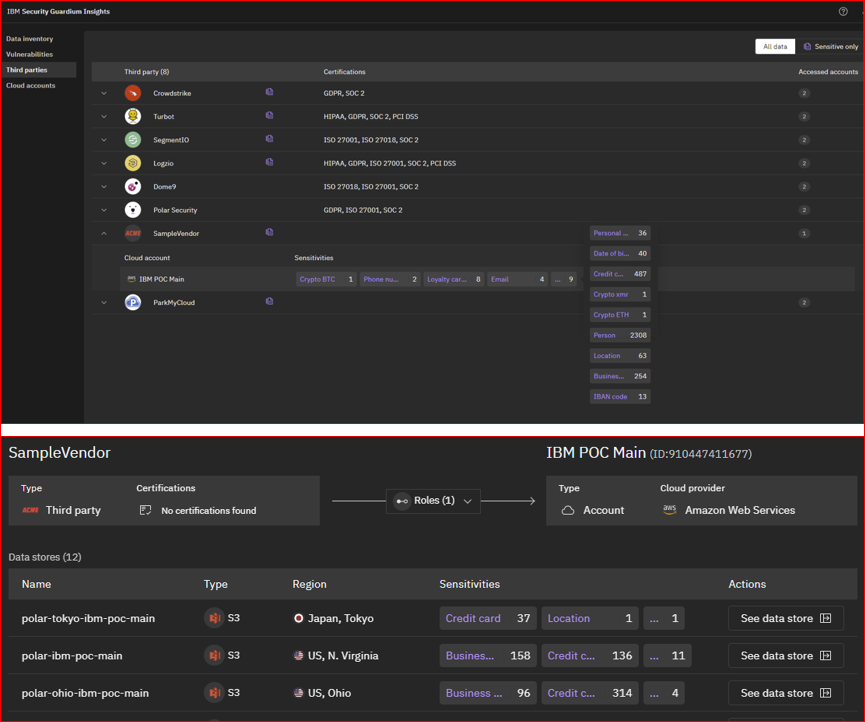
Figure 6: Third-Party Vulnerability Detection – This graphic identifies a vulnerability involving ‘SampleVendor,’ a third-party vendor erroneously granted access to sensitive data for which they lack appropriate certification. The depiction focuses on the scope of unauthorized access and its implications for data security.
- Jim: “Emily, we’re ready for your question.”
- Emily: “Can you tell me what cloud services IBM Security Guardium Insights SaaS DSPM scans?”
- Alex: “Certainly, Emily. IBM Security Guardium Insights SaaS DSPM scans various cloud data sources. It covers major cloud platforms like AWS, GCP, and Azure. Additionally, it integrates with various SaaS applications, including SharePoint, OneDrive, Slack, Google Drive, Jira, and Confluence. Its capability extends to locating and classifying the sensitivity of both structured (like databases) and unstructured data (like documents), ensuring comprehensive coverage is crucial for maintaining robust data security and compliance across diverse cloud environments.”
- Jim: “You know, Alex, this brings to mind the increasing adoption of hybrid cloud models. How does DSPM fit into this evolving landscape?”
- Alex: “Great point, Jim. Hybrid models add complexity, and DSPM helps by providing a unified view across all cloud environments.”
- Jim: “John, you’re on the air. What’s your question?”
- John: “What types of data sensitivities does Guardium Insights SaaS DSPM discover?”
- Alex: “John, Guardium Insights SaaS DSPM discovers a wide range of data sensitivities across four main categories: Personal Information, Development Secrets, Financial Information, and Identifiable Information. These include sensitivities like personal and business email addresses, AWS keys, GitHub tokens, credit card numbers, US bank numbers, and sensitive identifiers like US Social Security and driver’s license numbers.”
- Jim: “Linda, what would you like to know?”
- Linda: “How does it contribute to monitoring cloud databases?”
- Alex: “Linda, Guardium Insights SaaS DSPM contributes through discovery, data custodianship identification, classification, data flow mapping, and posture monitoring. It provides a 360-degree view of cloud database security.”
- Jim: “Tom, what’s your question, please?”
- Tom: “I’m wondering about the market trends and client requirements for cloud data security.”
- Alex: “Tom, several key areas are central to market trends and client requirements for cloud data security. First, there’s the widespread use of multi-cloud environments. This complexity increases the risk of exposing sensitive data. Additionally, there are challenges in managing ‘shadow data’—data that are not easily visible or controlled. Lastly, the high occurrence of cloud breaches significantly drives the need for robust security measures.”
- Jim: “Rachel, you’re next. What’s your question?”
- Rachel: “How does Guardium Insights SaaS DSPM support IBM’s strategic vision for data security?”
- Alex: “Rachel, Guardium Insights SaaS DSPM supports IBM’s strategic vision for data security by offering a comprehensive, integrated solution. It provides automated data inventory and discovery, enhancing visibility and security for known and shadow data stores. GI-SaaS DSPM tracks data movements to prevent leakage and actively addresses security vulnerabilities. Moreover, its seamless integration with major cloud platforms and SaaS applications ensures robust protection for cloud data. Its SaaS-native design allows for quick deployment, aligning with IBM’s commitment to efficient and effective data security.”
- Jim: “Kevin, let’s hear from you.”
- Kevin: “What are the key capabilities of Guardium Insights SaaS DSPM?”
- Alex: “Kevin, Guardium Insights SaaS DSPM offers key capabilities for cloud data security. These include automated inventory for known and shadow data stores, data movement tracking to prevent leakage, active remediation of security vulnerabilities, seamless integration with major data stores and SaaS applications, and quick, agentless deployment. Together, these features provide comprehensive visibility and robust protection for cloud data.”
- Jim: “Lisa, what’s on your mind?”
- Lisa: “Can you elaborate on IBM’s approach to data security?”
- Alex: “Certainly, Lisa. IBM’s approach to data security is multifaceted, focusing on end-to-end protection across the data lifecycle in hybrid cloud environments, including data classification and governance, leveraging threat intelligence and analytics, and providing robust cloud data security solutions. IBM emphasizes continuous monitoring, incident response, and compliance with regulatory standards. Additionally, IBM values collaboration and partnerships for enhancing data security and prioritizes educating employees and clients on security best practices. This comprehensive approach effectively addresses client-specific data security needs.”
- Jim: “Brian, what’s your question, please?”
- Brian: “Can GI-SaaS DSPM monitor third parties with set permissions on my organization’s cloud account?”
- Alex: “Brian, Guardium Insights SaaS DSPM can provide insights into third parties with set permissions on your organization’s cloud account. It identifies external vendors with access, detailing their roles, permissions, and the specific data stores and sensitivities they can access. It is crucial for understanding your security posture and guiding remediation efforts.”
- Jim: “Grace, what would you like to know?”
- Grace: “What resources does IBM provide for those interested in all Guardium Insights SaaS capabilities?”
- Alex: “Grace, IBM provides a comprehensive array of resources for those interested in Guardium Insights SaaS, including access to 30-day trials, detailed customer use cases, success stories demonstrating the solution’s impact, and opportunities for engagement with IBM’s security services and business partners. These resources thoroughly explain GI-SaaS capabilities and its practical applications in various settings.”
- Jim: “Marcus, you’re on the air. What’s your question?”
- Marcus: “How does it assist in compliance audits?”
- Alex: “Marcus, it aids by offering continuous monitoring, data protection controls, comprehensive compliance reports, remediation recommendations, and maintaining an audit trail.”
- Jim: “Anita, what’s your question?”
- Anita: “What integration capabilities does it offer for alerting and response?”
- Alex: “Anita, Guardium Insights SaaS DSPM offers robust integration with various cloud platforms and SaaS applications, enhancing alerting and response. This integration facilitates real-time monitoring and automatic alerts for data security incidents. GI-SaaS identifies various data risks in the cloud environment, including misconfigurations, shadow data, unauthorized data movement and access, compliance violations, and data vulnerabilities. DSPM enables proactive mitigation measures by pinpointing these risks, strengthening data security, and ensuring compliance. This comprehensive approach promptly addresses security issues, significantly enhancing the data protection framework.”
- Jim: “Thanks, Anita, for that insightful question, and Alex, for your detailed response on integration capabilities. Guardium Insights SaaS DSPM is a comprehensive tool for data security. Now, let’s briefly interlude to learn more about IBM’s Data Security Posture Management approach. We’ve got an informative segment from IBM that delves deeper into how their solutions empower organizations in data security. Stay tuned for this valuable insight.”
- Commercial Break from IBM: Data security posture management (DSPM) with Guardium Insights (1 minute)
Segment 4: Expert Insights [30:00-40:00]
- Jim: “Welcome back to the ‘Data Security Podcast.’ We’ve just gained insights into IBM’s approach to proactively managing data security posture management. Seeing how technology is evolving to address these critical needs is fascinating. Now, shifting gears back to our expert, Alex Johnson, we will explore some challenges and best practices in implementing DSPM solutions. Alex, based on your extensive experience, what are some common hurdles organizations face, and how can they effectively navigate these challenges?”
- Alex: “Thanks, Jim. When discussing IBM GI-SaaS DSPM, it’s essential to recognize its ability to simplify a complex data security landscape. IBM designed its DSPM to handle the diversity and volume of data in modern enterprises. It automates data discovery, classification, and inventory, eliminating the need for organizations to develop their piecemeal approach. It adeptly provides the means to manage data vulnerabilities, aligning compliance and security with company policies. Let’s explore some organizational best practices that will further improve vulnerability remediation challenges:”
- Data Governance and Ownership: Establishing clear data ownership and accountability is paramount, including defining roles and responsibilities for managing and protecting data aligned with organizational risk tolerance.
- Policies and Training: Developing comprehensive data security and privacy policies, keeping them up-to-date, and ensuring they cover third-party interactions. Regular awareness training is also vital to inform staff about data security best practices.
- Nuanced Remediation: Effective data vulnerability remediation is a function of organizational policy requirements. Establishing whether a data flow is valid or whether a particular third party should have access to specific sensitive content is established through organization data management and policies.
- Expertise in Cloud Environments: Leveraging the expertise of Managed Service Providers (MSPs) like CloudSecure Inc. can be invaluable for organizations lacking in-house expertise across various cloud platforms. They can manage the complexities and nuances of implementing and utilizing GI-SaaS DSPM across diverse cloud infrastructures.
- Alex: “By following these best practices, organizations can implement IBM’s DSPM solution effectively and improve their data security and compliance management capabilities.”
- Jim: “Alex, let’s discuss how GI-SaaS DSPM works in practice. Imagine a multinational corporation with data scattered across different regions and cloud platforms. How does DSPM step in?”
- Alex: “Great scenario, Jim. In such cases, GI-SaaS DSPM acts as a central command center. It monitors all data movements and access across these varied environments. Think of it as having a bird’s-eye view of your entire data landscape, regardless of where the data is or on which platform it resides.”
- Jim: “That sounds comprehensive. But what about real-time threats?”
- Alex: “That’s where its real-time data monitoring comes into play. GI-SaaS DSPM doesn’t just watch; It actively alerts the security team to unusual data movements or access patterns, swiftly identifying threats and minimizing potential damage.”
- Jim: “Regulatory compliance must be a nightmare in such complex environments.”
- Alex: “Indeed, but GI-SaaS DSPM simplifies it. It ensures data across all these regions adheres to relevant regulations, whether GDPR in Europe or other local data protection laws. It’s about ensuring compliance, no matter where your data resides.”
- Jim: “Data security is more than monitoring and compliance, right?”
- Alex: “Absolutely. GI-SaaS DSPM also monitors for encryption and access controls. It ensures that data stored in Asia, Europe, or the Americas is encrypted and accessible only by authorized personnel.”
- Jim: “And with data sovereignty becoming a hot topic?”
- Alex: “That’s where GI-SaaS DSPM’s data residency and sovereignty features shine. It allows organizations to dictate where their data is stored and processed, aligning with national data sovereignty laws.”
- Jim: “How does GI-SaaS DSPM respond to potential security incidents?”
- Alex: “It leverages advanced analytics and machine learning to detect threats and anomalies quickly, which means faster and more effective incident responses, significantly reducing the impact of any security breach.”
- Jim: “So, in essence, IBM Guardium Insights SaaS DSPM not only provides a panoramic view of data security across hybrid clouds but also ensures real-time monitoring, compliance, and proactive threat management.”
- Alex: “Exactly, Jim. It’s about bringing order, security, and compliance to what could otherwise be a chaotic data environment.”
- Jim: “That’s a comprehensive overview, Alex. This scenario-based understanding brings to light the critical role of GI-SaaS DSPM in managing data security complexities. Speaking of complexities, the IBM Cost of a Data Breach Report 2023 provides some eye-opening insights into data breaches’ risks and financial implications. Let’s take a quick commercial break to learn more about this report and how it can help businesses better manage data breach risks.”
- Commercial Break From IBM: Cost of a Data Breach Report 2023 – Get insights to manage better the risk of a data breach (1 minute)
Segment 5: Advanced Features and Future Outlook [40:00-50:00]
- Jim: “Welcome back, listeners. That report from IBM underscores the importance of robust data security strategies. Now, moving forward, let’s dive into Segment 5, where Alex will discuss the advanced features of GI-SaaS DSPM and its integration capabilities. This Segment is crucial for anyone looking to stay ahead in the rapidly evolving data security landscape. Alex, shall we?”
- Alex: “Certainly, Jim. Let’s explore how advanced GI-SaaS DSPM features are shaping the future of data security in hybrid cloud environments and beyond. IBM Guardium Insights SaaS DSPM enhances data security in hybrid cloud environments and across regions through the following mechanisms”:
- Centralized Data Monitoring and Management: GI-SaaS DSPM provides a centralized platform to monitor and manage data security across hybrid cloud environments and multiple regions. It allows organizations to gain a holistic view of their data assets, regardless of location or cloud platform. This centralization enables consistent security policies and controls, ensuring uniform data protection and compliance across different regions.
- Real-time Data Monitoring: GI-SaaS DSPM monitors real-time data access and movement, providing visibility into potential security threats and data breaches. It alerts security teams when abnormal activities occur, such as unauthorized access or unusual data movements across regions. By detecting and responding to these events promptly, organizations can minimize the impact of security incidents and prevent data loss.
- Regulatory Compliance: GI-SaaS DSPM helps organizations maintain compliance with data protection regulations in hybrid cloud environments and across regions. It provides robust data classification, inventory, and tracking capabilities, ensuring sensitive data is correctly identified, protected, and auditable. It helps organizations meet regulatory requirements, such as the General Data Protection Regulation (GDPR) or industry-specific regulations, regardless of the geographic location of their data.
- Data Encryption and Access Controls: GI-SaaS DSPM supports strong data encryption and access controls to enhance data security in hybrid cloud environments. It ensures that data is encrypted at rest and in transit, protecting it from unauthorized access. The system strictly enforces access controls, allowing organizations to define and implement appropriate data access permissions across various regions and cloud environments.
- Data Residency and Sovereignty: GI-SaaS DSPM enables organizations to control their data residency and sovereignty requirements. With the ability to deploy the solution in specific regions and control the storage and processing of data, organizations can comply with data sovereignty regulations and ensure data remains within desired areas.
- Threat Detection and Incident Response: GI-SaaS DSPM leverages advanced analytics and machine learning capabilities to detect potential threats and anomalies in data access and movement across hybrid cloud environments. It enables organizations to respond quickly and effectively to security incidents, mitigating risks and minimizing the impact on data security.
- By providing centralized monitoring, real-time data security, compliance capabilities, encryption, access controls, and incident response, IBM Guardium Insights SaaS DSPM enhances data security in hybrid cloud environments and ensures consistent protection across regions.
- Jim: “Alex, please share your thoughts on the future of data security and DSPM’s role.”
- Alex: “I’d be glad to Jim. The future of data security is rapidly evolving as organizations face increasingly sophisticated threats and regulatory requirements. In this rapidly changing landscape, GI-SaaS DSPM plays a crucial role by providing advanced capabilities to protect and manage data security effectively. Here are some aspects of the future of data security and GI-SaaS DSPM’s role”:
- Cloud Security and Compliance: As more organizations adopt cloud environments, data security and compliance become critical concerns. GI-SaaS DSPM will provide visibility, control, and compliance management across hybrid and multi-cloud environments. It will help organizations enforce consistent security policies, monitor data access and movement, and detect and respond to threats in real time.
- Data-centric Security: More than traditional perimeter-based security approaches are required. Data-centric security, which focuses on data protection, will become increasingly important. GI-SaaS DSPM will continue to enhance data classification, encryption, and access controls, ensuring that sensitive data is protected regardless of location or access.
- Automation and Artificial Intelligence: The volume and complexity of data make manual security management challenging. GI-SaaS DSPM will leverage automation and AI capabilities to streamline security operations, detect anomalies, and respond to potential threats faster. It will enable security teams to prioritize risks, automate remediation actions, and generate actionable insights to strengthen data security.
- Data Privacy and Governance: Data privacy regulations like GDPR have significantly raised the bar for organizations to manage and protect personal data. GI-SaaS DSPM will continue to play a vital role in helping organizations comply with data privacy regulations, including data discovery, classification, and monitoring. It will help organizations maintain data governance and demonstrate their commitment to privacy protection.
- Integration with Emerging Technologies: As organizations adopt emerging technologies like artificial intelligence (AI), the GI-SaaS DSPM will continuously adapt and integrate with emerging technologies, including the Internet of Things (IoT) and blockchain, to ingrain data security throughout their adoption. GI-SaaS DSPM will provide security and compliance oversight for data in these new technology ecosystems, offering visibility, control, and protection against data breaches.
- Alex: “In summary, the future of data security will revolve around GI-SaaS DSPM’s ability to provide comprehensive visibility, intelligent automation, and adaptive security measures to protect data in hybrid cloud environments. By addressing emerging challenges and integrating with new technologies, GI-SaaS DSPM will help organizations stay ahead of evolving threats, maintain compliance, and ensure data integrity and confidentiality.”
- Jim: “Alex, your insights into the future of data security and DSPM’s role are eye-opening. It’s clear that as technology evolves, so must our data security approaches. Speaking of staying ahead, IBM offers a unique opportunity for our listeners. Why not experience the power of DSPM firsthand? Let’s take a short break to learn about IBM’s 30-day DSPM trial, which could be the game-changer your organization needs.”
- Commercial Break From IBM: Start your 30-day DSPM trial (1 minute)
Segment 6: More Listener Call-In Questions [50:00-60:00]
- Jim: “Welcome back, everyone. I hope that commercial break got you thinking about the possibilities with DSPM. Now, let’s continue our conversation and take more questions from you; our listeners are where we get to address your real-world concerns and scenarios. Alex, are you ready for more questions?”
- Alex: “Definitely, Jim. Let’s hear what’s on the minds of our listeners.”
- Jim: “Derek, you’re our next caller. What’s on your mind?”
- Derek: “Can you share some key statistics regarding breaches and cloud security?”
- Alex: “Certainly, Derek. Some key statistics include that 77% of organizations store sensitive data in multi-cloud, 63% have exposed sensitive data in the cloud, 42% say at least half of their data is shadow data, and 45% of breaches occur in the cloud. These stats underscore the critical need for robust cloud security measures.
- Jim: “Helena, what would you like to ask?”
- Helena: “What are the benefits of using Guardium Insights SaaS DSPM for data security in the cloud?”
- Alex: “Helena, benefits include enhanced data visibility, improved compliance, efficient deployment, automated data inventory, and risk-based prioritization. These features collectively enhance cloud data security and protection, helping organizations mitigate risks and maintain compliance.”
- Jim: “Oliver, let’s hear your question.”
- Oliver: “How does the DSPM Analyzer function in the deployment architecture?”
- Alex: “Oliver, the DSPM Analyzer is key in Guardium Insights SaaS DSPM. It performs critical functions like data discovery, movement analysis, vulnerability detection, risk prioritization, and providing remediation recommendations, enabling organizations to secure their data effectively in the cloud.”
- Jim: “Rebecca, you’re next. What’s your question?”
- Rebecca: “What does IBM recommend for learning about Guardium Insights SaaS DSPM?”
- Alex: “Rebecca, IBM suggests visiting their product page for comprehensive information on Guardium Insights DSPM, including features, benefits, and customer success stories. It’s a valuable resource for deepening your understanding of the solution.”
- Jim: “Moving on, we have Ethan. Ethan, what’s your question?”
- Ethan: “Hi, Jim. How does Guardium Insights SaaS DSPM adapt to evolving data security threats in the cloud?”
- Alex: “Ethan, it adapts through continuous monitoring, advanced analytics, and integration with threat intelligence sources. These capabilities ensure Guardium Insights stays ahead of evolving threats, providing robust and proactive data security.”
- Jim: “Next up is Mia. Mia, what would you like to ask?”
- Mia: “How does Guardium Insights SaaS DSPM protect data during its automated discovery process?”
- Alex: “Mia, Guardium Insights SaaS DSPM employs several strategies to protect data during the automated discovery process. Firstly, it operates without agents, avoiding any impact on your critical business applications. The solution deploys minimal cloud assets, reducing exposure and attack surface. It securely inventories and classifies data using mechanisms that analyze metadata without accessing the data content. Continuous monitoring detects vulnerabilities and potential compliance violations by tracking data movements and access patterns. Furthermore, it prioritizes risks, focusing on critical issues for efficient resource allocation in remediation. These measures ensure robust data protection throughout the discovery phase, minimizing business disruption while securing sensitive information.”
- Jim: “Tony, you’re on the line. What’s your question?”
- Tony: “What compliance standards or regulations does Guardium Insights SaaS DSPM help organizations adhere to?”
- Alex: “Tony, it helps with several, including GDPR, PCI DSS, HIPAA, SOX, and regional data protection laws. Its capabilities ensure organizations can meet these diverse compliance requirements effectively.”
- Jim: “Sophia, what’s on your mind?”
- Sophia: “Can you share the types of vulnerabilities GI-SaaS DSPM identified for clients?”
- Alex: “Sophia, GI-SaaS DSPM identifies two primary types of client vulnerabilities: Security data vulnerabilities and Compliance data vulnerabilities. Under Security data vulnerabilities, it detects issues like unencrypted data stores, sensitive data duplication flows, default write entitlements on data stores and potential or actual data flow between cloud accounts. Compliance data vulnerabilities alert on exposed sensitive data, potential or actual cross-country data flow, and non-compliance issues due to lack of backups. These capabilities enable clients to address security and compliance challenges in their cloud environments.”
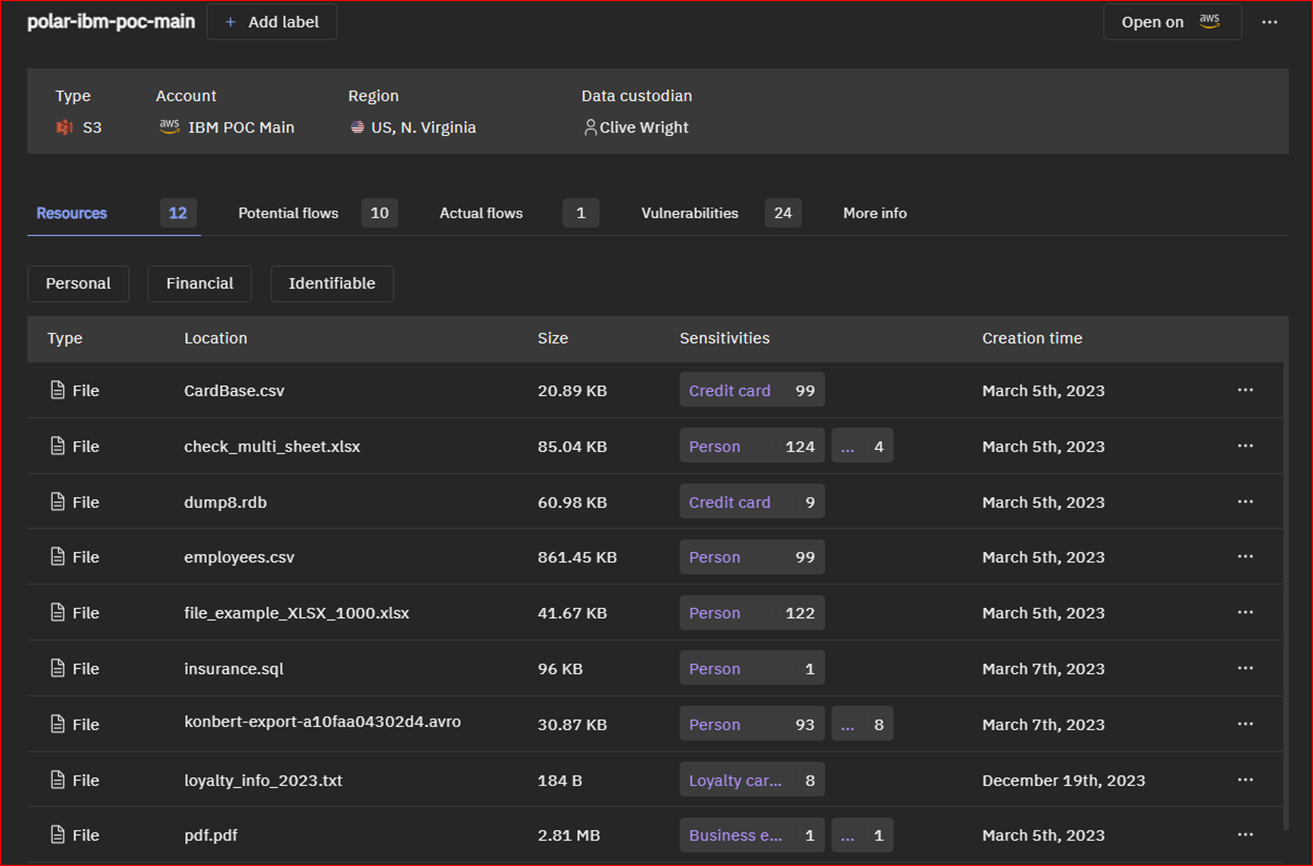
Figure 7a: An AWS S3 bucket contains ten ‘potential’ sensitive data flows and one ‘actual’ (confirmed) sensitive data flow, indicating a need to investigate whether these are intentional or due to a cloud misconfiguration vulnerability.
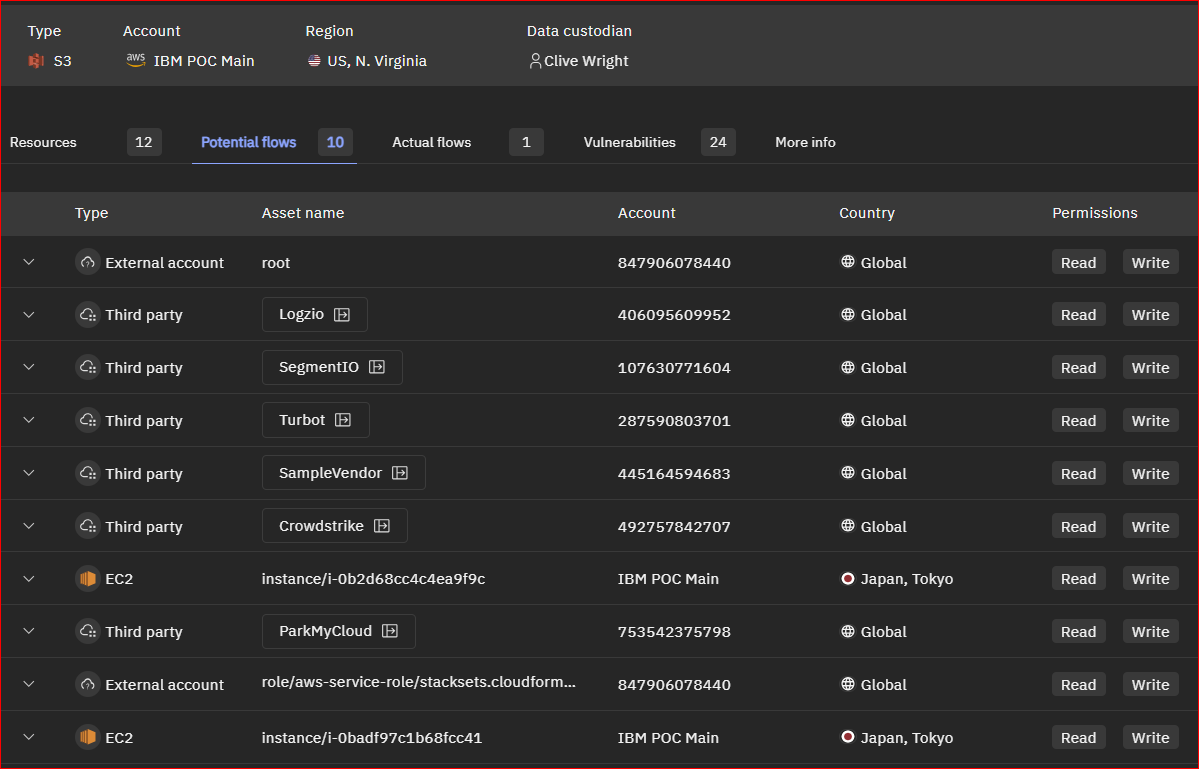
Figure 7b: Shows the same AWS S3 account as in Figure 7a with focus on the ten potential read/write access flows to external accounts. A ‘potential flow’ represents a configuration allowing the movement of sensitive data, though no such movement has occurred yet.
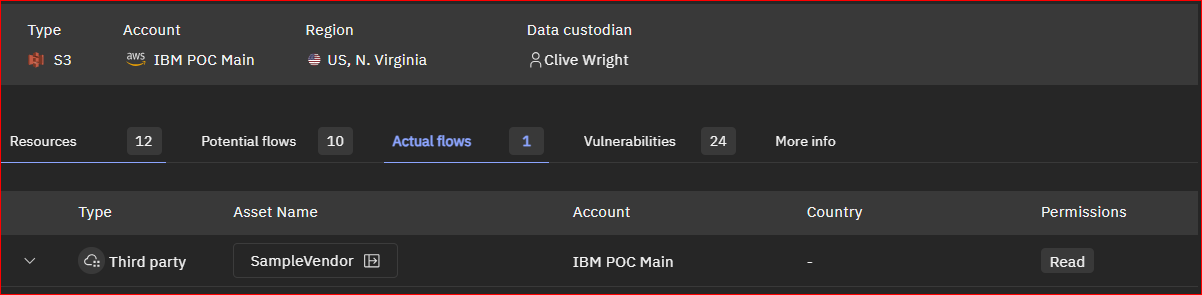
Figure 7c: Displays the same AWS S3 account as in previous figures, focusing on a single actual flow of sensitive data to a third party with read access. An actual flow signifies a data movement event that has already taken place.
- Jim: “Oliver, let’s hear your question.”
- Oliver: “What role does data custodianship identification play in Guardium Insights SaaS DSPM’s capabilities?”
- Alex: “Oliver, data custodianship identification is crucial. It helps assign responsibility for data, implement access control, ensure compliance during audits, and facilitate efficient incident response. It’s key to maintaining accountability and protecting sensitive information.”
- Jim: “Rebecca, what’s your question?”
- Rebecca: “What specific actions does Guardium Insights SaaS DSPM recommend for remediation of data vulnerabilities and compliance violations?”
- Alex: “Rebecca, it recommends enhancing data access controls, implementing encryption, fine-tuning DLP policies, conducting user training, and guiding compliance remediation efforts. These targeted actions are essential for addressing vulnerabilities and compliance issues effectively.”
- Jim: “Ava, what would you like to know?”
- Ava: “How does Guardium Insights SaaS DSPM enhance the monitoring of data transactions between countries?”
- Alex: “Ava, it enhances this monitoring by continuously collecting data movement information, classifying data, and discovering shadow data, which helps manage cross-border data transfers and adhere to international data transfer regulations.”
- Jim: “Jacob, what’s your question?”
- Jacob: “What specific features or capabilities make the deployment of Guardium Insights SaaS DSPM fast and automated?”
- Alex: “Jacob, key features include quick and easy deployment, minimal cloud assets needed, zero-performance impact, automated data inventory, and continuous monitoring. These aspects make deployment efficient and user-friendly.”
- Jim: “Sophia, what’s your question?”
- Sophia: “How does Guardium Insights SaaS DSPM facilitate engagement with IBM consulting, security services, and business partners?”
- Alex: “Sophia, it facilitates engagement through solution expertise, implementation support, customization, training programs, and ongoing support. These engagements ensure successful deployment and optimization of the solution.”
- Jim: “Ethan, what’s your question?”
- Ethan: “Are there any known challenges associated with deploying Guardium Insights SaaS DSPM?”
- Alex: “Ethan, challenges can include data integration, configuration, customization, ensuring data classification accuracy, managing user adoption, and scalability. However, proper planning and IBM’s expert support can effectively manage these challenges.”
- Jim: Alex, as we wrap up, please share some final thoughts and a key takeaway from your experience that stands out.
- Alex: “Certainly, Jim. Guardium Insights SaaS DSPM addresses data sprawl and shadow data, providing complete visibility and enabling prevention of data leakage and compliance violations. The key Takeaways to understand about GI-SaaS DSPM are:”
- Automated data inventory and discovery are crucial for identifying and protecting sensitive data in diverse cloud workloads and SaaS applications.
- The solution’s seamless integration with AWS, Azure, GCP, and various SaaS applications simplifies the security management process.
- SaaS-native deployment ensures no impact on critical applications and quick provisioning for immediate value.
- Maintaining a solid data security posture and minimizing compliance violations are achievable with tailored compliance reports and active remediation features.
- The comprehensive approach of Guardium Insights SaaS DSPM reduces the attack surface in cloud environments.
- Alex: “Also, I want to share a compliance case we handled at CloudSecure Inc. We worked with a large, well-known healthcare provider who needed help with data sprawl across multiple cloud platforms. DSPM was a new service we had recently added to our managed service, and we were curious to see its impact, given we knew our client managed quite a bit of sensitive data. After implementing Guardium Insights SaaS DSPM, we streamlined their data security and brought them into full compliance with healthcare data regulations. It was a game-changer for them, reducing risks and enhancing data management efficiency.”
- Jim: “That’s a powerful story, Alex, and a testament to the practical impact of DSPM solutions. Thanks for sharing your expertise and experiences with us today.”
- Alex: “It’s been my pleasure, Jim. Sharing these stories brings the real-world applications of these solutions to life.”
Concluding Segment [60:00-62:00]
- Jim: “To everyone tuning in, consider how Guardium Insights SaaS DSPM might revolutionize your approach if facing Cloud data security challenges. You should browse the IBM website and think about how to actively engage with the DSPM team or start with the GI-SaaS DSPM 30-day trial in your cloud environment.”
- Jim: “Next week, we’re delving into AI in cybersecurity. We’ll explore how this technology evolves and revolutionizes our approach to digital threats. You will want to take advantage of this cutting-edge discussion.”
- Jim: “Your thoughts and feedback on today’s episode are invaluable to us. Share your perspectives or questions on our social media or email us. It’s your insights that enrich our podcast and community.”
- Jim: “A heartfelt thank you to our production team for making this podcast a reality, and a special shoutout to you, our listeners. Your engagement is what drives our mission to demystify data security.”
- Jim: “We hope today’s episode has shed light on the critical role of DSPM in cloud security. Remember, navigating data security is a continuous journey. For more insights on IBM Guardium Insights SaaS DSPM, check out the resources on IBM’s website. Stay tuned for our next episode, where we tackle more cutting-edge trends in data security. Thanks for joining us, and we’ll catch up with you next time on the ‘Data Security Podcast.’”