Enterprise Architecture (EA), established by John Zachman in the mid-1980s, addresses the complexities of distributed technology systems. Recognized as a crucial discipline within the business and information technology sectors, EA has gained prominence, especially in a landscape reshaped by digital disruption. It is a strategic framework that guides organizations through the intricate business and digital environments, helping leaders navigate challenges and capitalize on opportunities.
Introduction
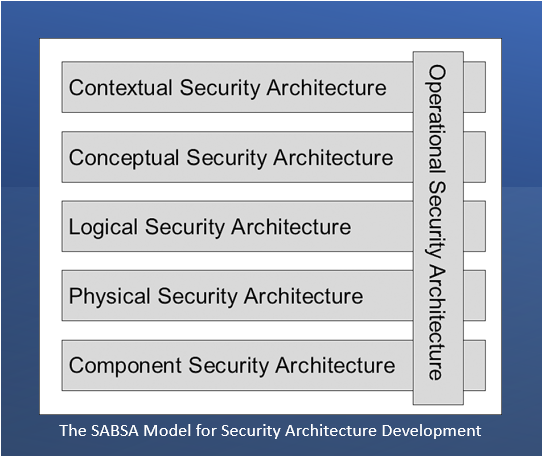
SABSA is a risk-driven methodology for developing enterprise security architectures that align with business needs. Originating independently from the Zachman Framework, it adopts a holistic approach, deriving security measures directly from an organization’s requirements and goals. The framework’s unique multi-layered structure, comprising contextual (business objectives and risk strategies), conceptual, logical, physical, component, and operational layers, facilitates a comprehensive approach to security. This structure ensures that security measures are deeply integrated with critical business functions and aligns risk management with IT architecture methods across the enterprise.
By focusing on effective protection and adaptability, SABSA enables organizations to address evolving threats and comply with strategic and regulatory requirements. Its global application across various sectors underscores SABSA’s versatility and capability to enhance operational efficiency by identifying and consolidating duplicate security components. Unlike commercial products, SABSA is an open-use methodology that fosters stakeholder collaboration and ensures a clear understanding of security needs and solutions.
The Open Group Architecture Framework (TOGAF) provides a comprehensive methodology and tools for developing and governing enterprise information technology architectures aligned with business goals. With origins in US Department of Defense frameworks, TOGAF facilitates systematic, iterative architectural design across four levels: Business, application, data, and technology. Key benefits include helping organizations define, organize, and standardize requirements to reduce errors, meet budgets, and ensure IT meets business needs.
As the most utilized enterprise architecture framework, TOGAF offers a reusable set of assets and uniform standards powered by The Open Group’s global open standards consortium. At its core, TOGAF enables enterprises to create adaptable architectures that drive digital transformation strategies, with a structure promoting governance and stakeholder communication throughout iterative planning and implementation.
The Essence of Enterprise Security Architecture (ESA)
Businesses today rely on a vast network of software, data, and interconnected devices to operate. Protecting this digital frontier is critical. That’s where Enterprise Security Architecture (ESA) comes in. ESA is the strategic framework that guides how a company safeguards all its digital assets. ESA is employed to defend against modern cyber threats with proactive security strategies.
The relationship between business goals and the right security tools is critical when businesses navigate a complex software, data, and device network. The digital landscape presents challenges and opportunities for growth, making the strategic integration of Enterprise Security Architecture (ESA) essential for survival. ESA is a blueprint for safeguarding a company’s digital assets against evolving cyber threats, ensuring comprehensive protection and stakeholder confidence.
Artificial Intelligence (AI) and Machine Learning (ML) Empowered ESA
Enterprise Security Architecture (ESA) is a comprehensive framework for managing an organization’s cybersecurity strategy. It focuses on integrating various security measures and technologies to protect digital assets from threats and vulnerabilities. To create a more robust defense mechanism, ESA combines traditional security practices with innovative technologies like artificial intelligence (AI) and machine learning (ML).
AI and machine learning play a significant role in enhancing ESA by offering advanced capabilities for predictive threat detection. These technologies analyze patterns and behaviors in data to identify potential security threats before they can cause harm. For example, AI can monitor network traffic in real-time, detecting anomalies that may indicate a cybersecurity threat. Machine learning algorithms learn from past incidents, improving their ability to predict and identify future threats.
This integration of AI and machine learning with foundational security measures ensures that ESA is not just reactive but also proactive. It enables organizations to stay ahead of cybercriminals by predicting and mitigating potential security breaches before they occur. By aligning cutting-edge trends with traditional security frameworks, ESA provides a holistic approach to protecting an organization’s digital assets, ensuring data integrity, confidentiality, and availability.
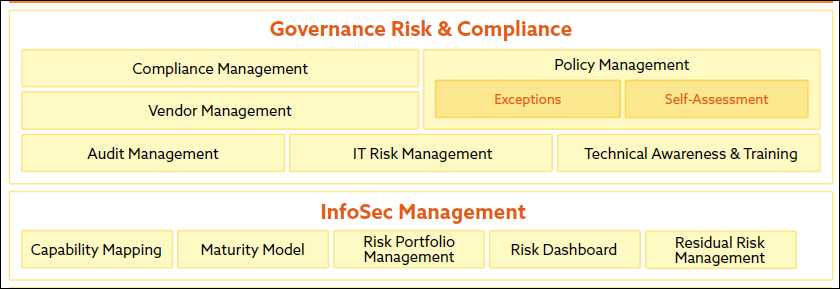
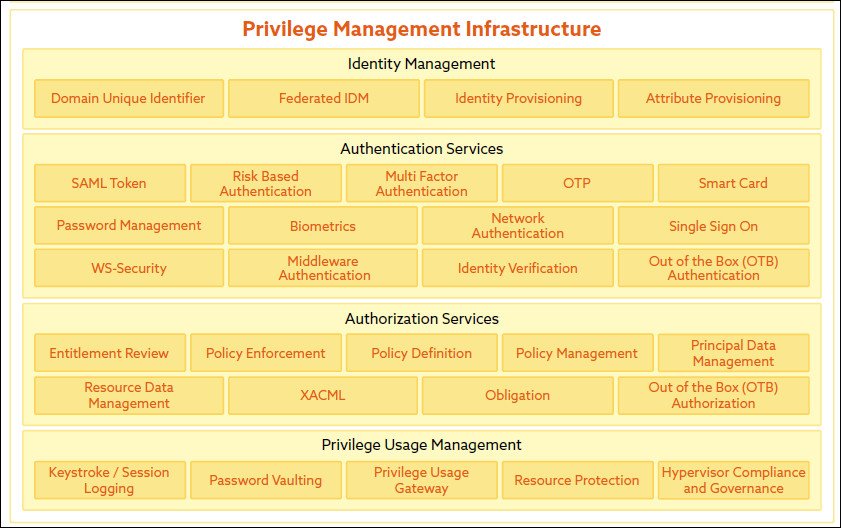
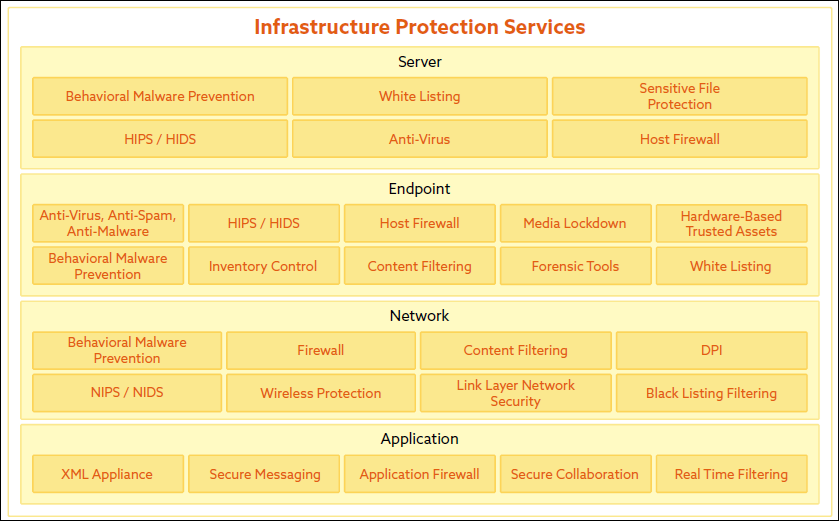
The ESA Section of the CSA Enterprise Architecture (EA)

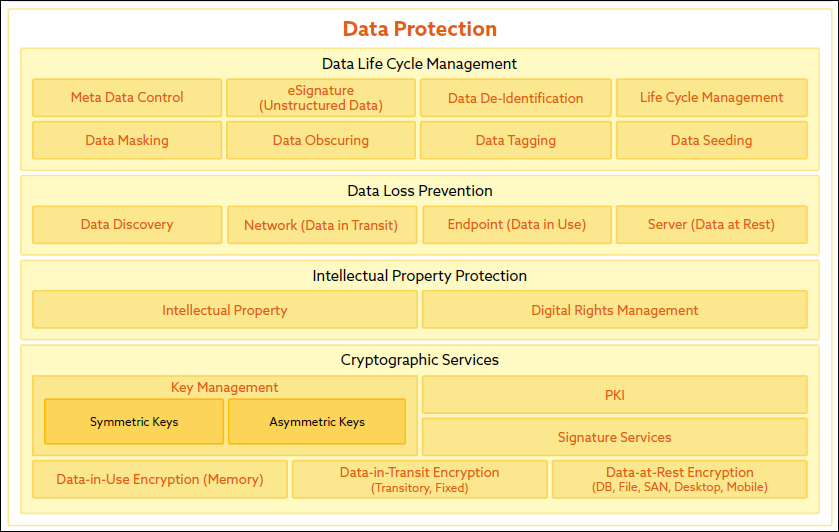
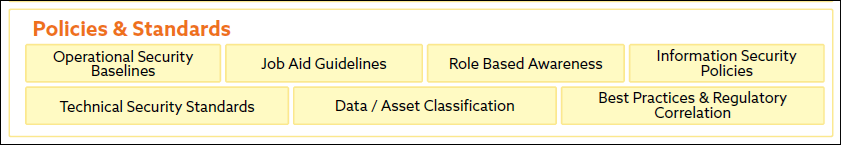
Impact of Digital Transformation
Digital transformation signifies a comprehensive overhaul of business and organizational activities, processes, competencies, and models to fully leverage the changes and opportunities of a mix of digital technologies and their accelerating impact across society in a strategic and prioritized way. This transformation journey highlights the crucial role played by Enterprise Architects (EAs) in bridging the gap between technology solutions and business goals.
Enterprise Architects are at the forefront of digital transformation efforts. They possess a unique blend of technical knowledge and business acumen, enabling them to design and implement technology solutions that align with and drive the business objectives forward. Their strategic role involves:
- Mapping out complex digital ecosystems.
- Identifying the technology that will deliver the greatest value.
- Charting a path that balances innovation with practicality.
As businesses navigate the intricacies of digital expansion, security stands out as a paramount concern. The digital landscape continuously evolves, leading to the emergence of new threats as technology advances. Enterprise Architects (EAs) actively ensure the robustness, currency, and seamless integration of security measures with the technological frameworks adopted. They work to create a secure digital environment where business operations can thrive without being hindered by the risk of cyber threats.
In essence, Enterprise Architects are key players in the digital transformation journey, guiding organizations through the complexities of modernizing their operations. They ensure that integrating new technologies leads to enhanced efficiency, better customer experiences, and a stronger competitive edge in the market. Their ability to align technological innovation with business strategies ensures that organizations can confidently navigate the digital age.
Transformative Shift in Security Technologies
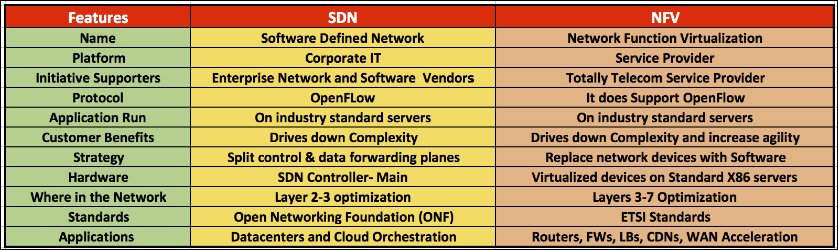
The landscape of security technologies is witnessing a transformative shift with the integration of Network Functions Virtualization (NFV), Software-Defined WAN (SD-WAN), and cloud computing. These advancements redefine how security architectures can adapt to the needs of an increasingly digital and remote workforce.
Network Functions Virtualization (NFV): Flexibility at the Forefront
NFV enables the virtualization of network security functions like firewalls and intrusion detection systems. This shift from hardware-based models allows organizations to architect, deploy, and scale security defenses with unprecedented agility and flexibility.
Key benefits include rapidly deploying new services in response to emerging threats, efficiently scaling protection based on demand, and customizing security strategies to address specific risks. NFV also encourages innovation by freeing developers from hardware constraints.
Integrating NFV capabilities into enterprise security architectures enhances resilience and threat response. Organizations can instantly distribute security functions across their dynamic networks to reduce failure points. The simplicity of deploying virtualized, software-defined security controls also allows for rapid, targeted responses to vulnerabilities.
For instance, we can deploy virtual firewalls instantly across the network, providing immediate protection to critical assets without needing additional physical hardware. This adaptability makes NFV Critically valuable for securing cloud environments and distributed networks.
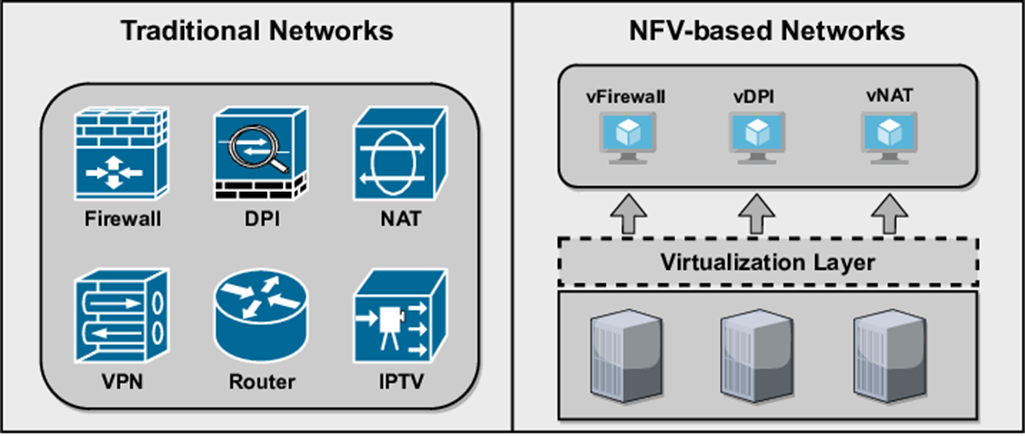
Software-Defined WAN (SD-WAN): Streamlining Secure Connectivity
SD-WAN revolutionizes secure connections across the organization, employing encrypted tunnels over the internet for seamless and secure data flow. This technology cuts costs and simplifies the enforcement of unified security policies, ensuring consistent protection across all locations. SD-WAN optimizes network performance and availability by leveraging encrypted tunnels over the internet to transmit data securely across diverse locations. By intelligently routing traffic based on business priorities and real-time conditions, SD-WAN ensures high-bandwidth applications receive the required speed and reliability. This software-defined approach simplifies network management through centralized control and enhances security threat response through comprehensive visibility. As businesses adopt cloud services and support remote workers, SD-WAN’s capacity to provide efficient, adaptable connectivity makes it critical for establishing secure, resilient networks.
Cloud Computing: Security Beyond Boundaries
The shift to cloud computing requires rethinking security strategies to protect data and applications outside traditional boundaries. In enhancing our cloud security posture through Enterprise Security Architecture (ESA), we integrate strategic principles to address the nuanced risks of cloud computing. We focus on deploying identity and access management (IAM) systems, robust encryption techniques, and comprehensive incident response strategies. These elements are pivotal in crafting a secure cloud architecture that mitigates risks like data breaches and unauthorized access. Within this framework, Cloud Access Security Brokers (CASBs) actively offer visibility and control, safeguarding our data across all cloud services and embodying our commitment to a resilient and adaptive cloud security strategy.
Embracing these technological shifts enables organizations to strengthen their security postures, ready to tackle future cyber challenges with resilience.
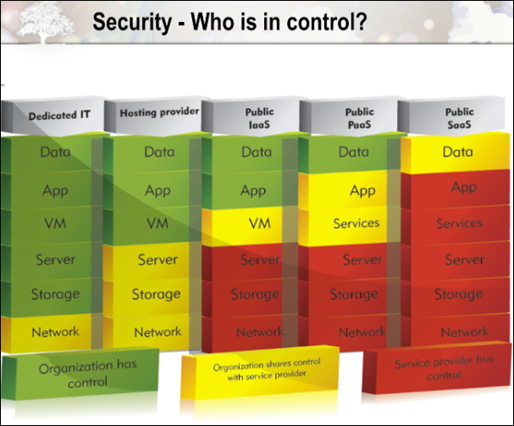
Conclusion
Throughout this discussion, we’ve navigated the intricate evolution of enterprise security architecture, underscoring its vital role in an increasingly digital and vulnerable world. By weaving together strategic frameworks, advanced technologies, and a keen awareness of cyber threats, organizations are better poised to defend and align their digital aspirations with a comprehensive security posture. The symbiosis between business strategies and security initiatives not only shield against risks but also empower business continuity and innovation.
As enterprises evolve, stakeholders must champion the fusion of agility, foresight, and collaboration within their security practices to foster resilience in the face of unrelenting cyber threats. The resources provided through the OSA Framework offer valuable insights and guidance for those looking to delve deeper and fortify their enterprise security architecture. By embracing such robust methodologies, businesses can transform their security paradigms, ensuring they are at the forefront of defense—an offensive strategy—against tomorrow’s security challenges. To explore the benefits of aligning your security architecture with business goals, discover the potential of the OSA Framework here.
FAQs
1. How has enterprise architecture evolved? Enterprise architecture has undergone significant changes, particularly in the 21st century. Initially focusing on IT-centric frameworks, it has transitioned to more inclusive models that treat the enterprise as interconnected. This evolution emphasizes integrating all business processes, stakeholders, and technology infrastructure to create a unified approach.
2. What are the steps to becoming a security architect? To become a security architect, one should develop strong technical and analytical skills, acquire knowledge of industry standards and regulations, and gain experience in information security. Professional certifications like the Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), or CompTIA Security+ are often prerequisites for the role.
3. What constitutes an enterprise security architecture framework? An enterprise security architecture framework consists of systematic guidelines and principles designed to structure the security architecture of a business at various levels. Organizations may create unique frameworks by blending elements from established international standards, such as The Open Group Architecture Framework (TOGAF) and the Sherwood Applied Business Security Architecture (SABSA).
4. How do the TOGAF and SABSA frameworks differ? TOGAF and SABSA are frameworks that complement each other, with TOGAF providing a more expansive view of enterprise architecture across multiple domains. At the same time, SABSA specifically concentrates on the security aspects of architectural design. TOGAF offers a holistic approach to the enterprise, whereas SABSA zeroes in on security architecture.